Pre-Launch Security Checklist: Are You Really Ready to Go Live?
Secure your Web3 project with this comprehensive pre-launch security checklist. Covers smart contracts, wallets, APIs, and more.

Security Checklist for Pre-Launch (Web3)
Smart Contract Security
Smart Contract security is crucial in web3 projects to ensure the integrity of decentralized applications and prevent exploits.
- Conduct a thorough security audit of smart contracts using reputable audit firms.
- Implement proper access controls for smart contracts to prevent unauthorized access.
- Ensure that smart contract code is open-source and publicly available for review.
- Ensure that smart contract code follows industry-standard security practices like the OpenZeppelin library.
- Implement checks and balances for smart contract upgrades to prevent unauthorized modifications.
Wallet Security
Wallet security is essential for protecting the private keys used to access digital assets and transact in web3 environments.
- Provide clear instructions for users to secure their wallets and private keys.
- Recommend the use of hardware wallets for added security.
- Implement multi-signature functionality to require multiple approvals for transactions.
- Implement time-based withdrawal limits for wallets to prevent large withdrawals quickly.
Web3 API Security
Web3 API security is necessary to prevent unauthorized access to sensitive user data and ensure the confidentiality and integrity of interactions with decentralized applications.
- Implement rate limiting to prevent DDoS attacks on the API.
- Implement API authentication and authorization to prevent unauthorized access.
- Implement encryption for all data in transit using HTTPS.
- Implement input validation and sanitization to prevent injection attacks.
Node and Infrastructure Security
Node and infrastructure security is vital to protect the underlying infrastructure and prevent attacks on the network and its participants.
- Ensure that all infrastructure components are up-to-date with the latest security patches.
- Implement firewall rules to restrict access to the server to only necessary IP addresses or ranges.
- Implement secure communication protocols such as SSH and TLS for all infrastructure components.
- Implement proper access controls for all infrastructure components to prevent unauthorized access.
Data Security and Privacy
Data security and privacy are critical to protect user information and prevent data breaches, especially given the decentralized nature of web3 applications.
- Implement a data backup strategy to prevent data loss in case of server failure or other disasters.
- Ensure that all sensitive data is stored securely and encrypted at rest.
- Implement a privacy policy and ensure that users have consented to it.
- Implement GDPR or CCPA compliance measures if applicable.
- Review third-party integrations and ensure they are secure and adhere to data protection laws.
Incident Response
Incidence response is necessary to mitigate the impact of security incidents, identify the root cause of the breach, and implement measures to prevent similar incidents in the future.
- Develop and document an incident response plan to prepare for and respond to security incidents.
- Ensure all staff members know the incident response plan and their roles and responsibilities.
- Implement a system to monitor security incidents and notify the appropriate staff members.
- Conduct regular security assessments and penetration testing to identify vulnerabilities and potential threats.
Legal Compliance
Legal compliance is essential to ensure that web3 projects comply with applicable laws and regulations, such as those related to securities, data protection, and anti-money laundering.
- Ensure that the project complies with all applicable laws and regulations, such as data protection, privacy, and accessibility laws.
- Ensure that all terms of service and privacy policies are clear, accurate, and up-to-date.
- Obtain any necessary legal disclaimers or licenses if applicable.
User Education
User education is important in web3 projects to help prevent security incidents and improve overall security by informing users about risks and best practices.
- Provide clear and concise information about the project's security practices, such as wallet security, smart contract security, and data protection policies.
- Educate users on best practices for wallet management and other security measures.
- Provide clear instructions on what to do in case of a security incident.
By following this pre-launch security checklist for a web3 project, you can ensure that your project is secure and protects your users' sensitive data and funds. Remember, security is an ongoing process, so it's essential to conduct regular security assessments and testing to identify and address any new vulnerabilities or threats.
We're excited to announce the launch of Quillshield, a suite of AI-powered tools designed to strengthen your smart contract security!
Quillshield offers an additional layer of protection alongside our security audits, helping you identify and address potential vulnerabilities before deployment.
Leverage Quillshield for:
- Early-stage bug detection
- Automated code analysis
- Enhanced code clarity and efficiency
Get a Free AI-Powered Smart Contract Audit with QuillShield - Click Here
Thank you for taking the time to review this pre-launch security checklist and QuillSheild Ai Powered Smart Contract tool. We hope this document has helped ensure your product launch goes smoothly and securely.
If you are looking for a security audit of your product, we would be happy to help. Our team of experienced security professionals can provide a comprehensive audit of your product's security posture to identify any potential vulnerabilities and provide recommendations for improvement.
QuillAudits’ Impact
QuillAudits has audited over a million lines of code across 1400+ projects, securing over $30B AUM. We supercharge web3 security with our product suite, consisting of AI-driven audit, token risk assessment, and monitoring tools. Supporting 15+ blockchains, our team prioritizes holistic evaluation and excellence in safeguarding digital assets.
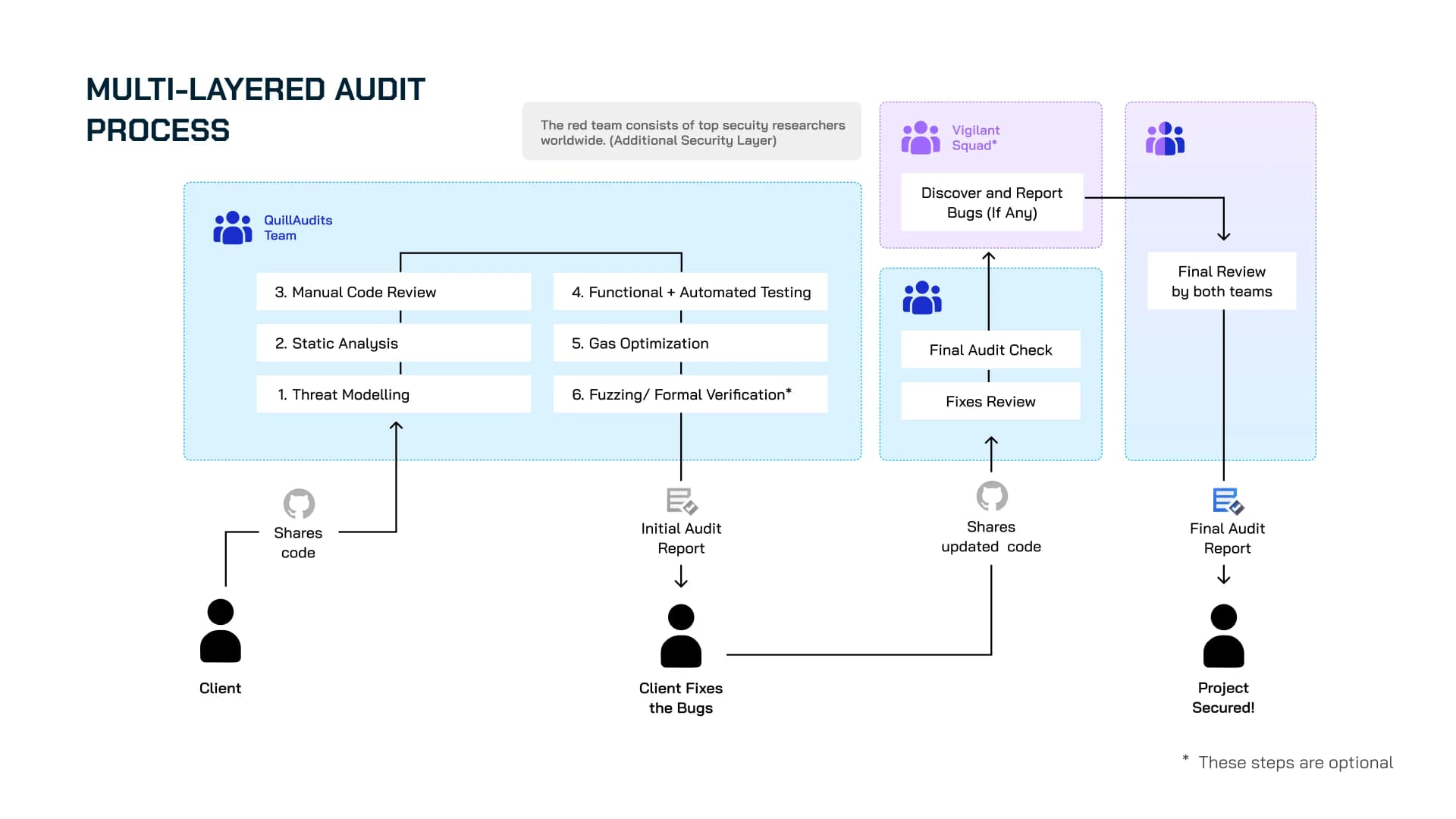
Audit Process
Our Multi layer process is thorough and constantly updated to address the latest vulnerabilities. We employ a combination of manual line-by-line review and automated testing to identify any issues within the code.
Our Clients & Partners
Successfully audited over 1400 projects over the span of 7+ years, catering to their security needs with our robust infrastructure and cost-effective solutions.
We're armed with strategies and solutions for all EVM-compatible chains, and below are some of them. While we could list over 100 supportive chains, we've opted to showcase only the most prominent ones.
We are ecosystem partners for some of the top industry leaders and projects that are shaping the future of Web3 with a non-exhaustive display shown above. Our growth is a product of continuous support from our ecosystem partners, community and team.

Audit Report - QuillAudits_Report
Audit Walkthrough - QuillAudits_Walkthrough
Contents



