
Before QuillAudits
- Exploits like reentrancy and front-running can let attackers withdraw extra funds and manipulate transaction timing for unfair gains
- Vulnerabilities could allow users to mint CDP tokens or pension shares indefinitely, disrupting the system's economic balance.
After QuillAudits
- Ensure precision in decimal handling with standard libraries, recalculate accurately, fix logic errors, and secure referral systems against exploitation.
- Implementation of reentrancy protection mechanisms.
Get an Audit done today for your Smart Contract
Join 1500+ leaders who secured themselves from losing Billion Dollars


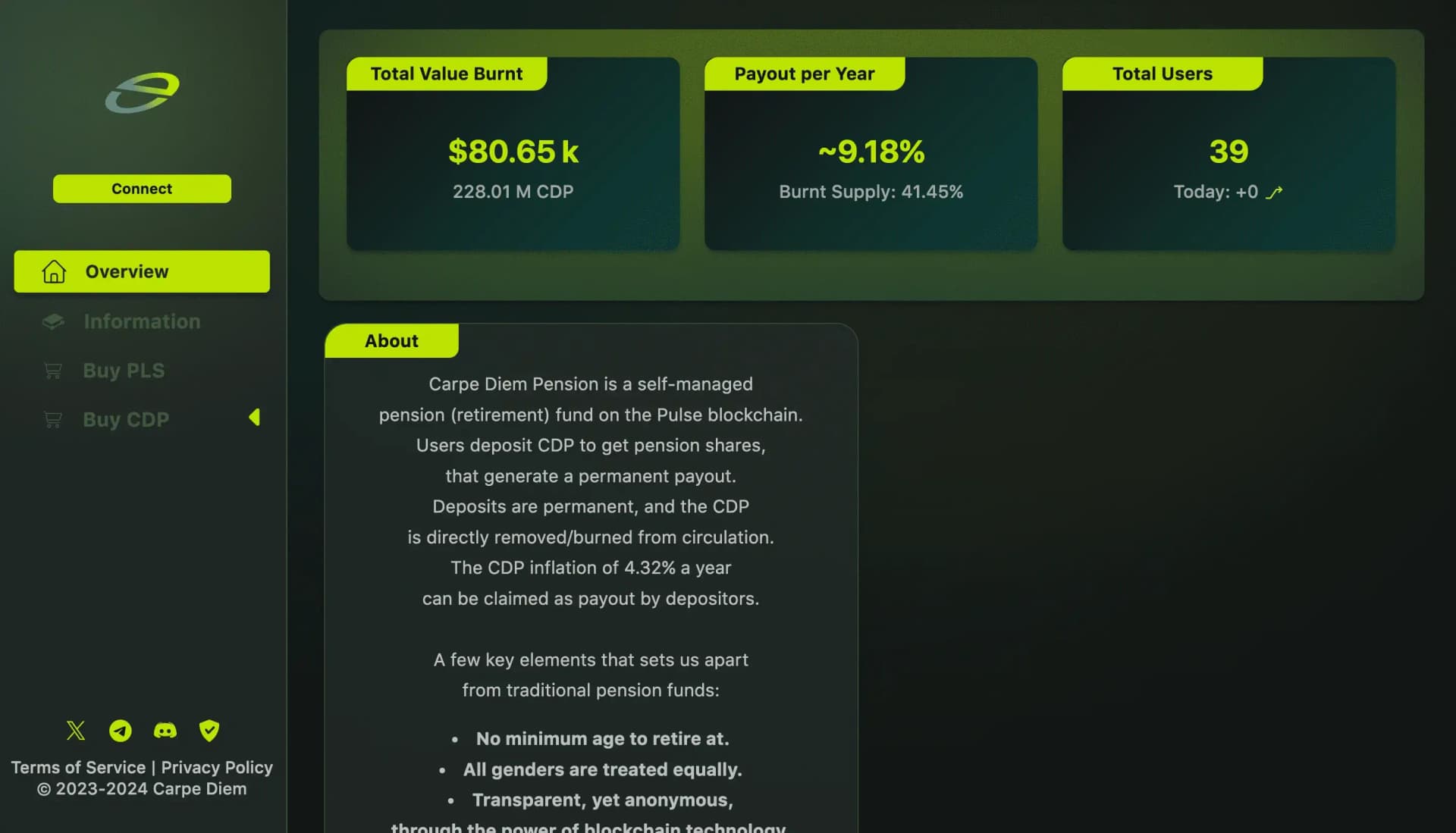
Carpe Diem Pension, on Pulse blockchain, redefines retirement with a self-managed, inclusive, globally portable fund. Unique for its token burn mechanism, it ensures a sustainable 4.32% inflation payout. With $143.11k and 41.06% of CDP already burned, it serves 35 users globally.
CarpeDiem Pension's Flexible, Blockchain-Enabled Future
CarpeDiem Pension redefines retirement planning with a unique approach that deviates from traditional pension funds. With no minimum age for retirement, it offers flexibility and freedom, ensuring all genders receive equal treatment. CarpeDiem Pension ensures blockchain transparency, anonymity, and global accessibility, safeguarding pensions during international relocation. Easily transfer pensions to loved ones; share wallet access. Re-deposit payouts for increased future benefits. Importantly, CarpeDiem Pension prioritizes deposit security by avoiding utilizing client funds for internal investments. To become a part of this forward-thinking pension scheme, one simply needs to install and configure a blockchain wallet.
CarpeDiem Pension's Challenges: Enhancing Security Against Reentrancy, Front-Running, and Infinite Minting
CarpeDiem Pension confronts critical security challenges, including the risks of reentrancy and front-running exploits.Malicious actors may exploit contract vulnerabilities, withdrawing excess funds or manipulating transaction timing for unfair advantages. System faces infinite minting threats, risking economic stability with endless creation of CDP tokens or pension shares. Addressing these challenges is paramount to safeguarding the integrity and security of CarpeDiem Pension.

CarpeDiem Pension's Journey Through our Audit Process
- Information gathering:
- Collected and reviewed all relevant documentation, including whitepaper, technical specifications, and design documents.
- Obtained a clear understanding of the CDP platform's functionality, economic model, and intended user interactions.
- Discussed client concerns and specific areas of focus for the audit.
- Manual Code Review:
- Conducted a line-by-line review of the smart contract code, focusing on:
- Vulnerability identification: Searching for known vulnerabilities like reentrancy, front-running, integer overflows, and access control issues, etc.
- Vulnerability identification: Searching for known vulnerabilities like reentrancy, front-running, integer overflows, and access control issues, etc.
- Tokenomics correctness: Verifying if the code accurately implements the intended economic model and token distribution mechanisms.
- Solidity best practices: Compliance with secure coding standards and adherence to established guidelines.
- Functional Testing:
- Developed and executed a comprehensive set of test cases covering various user interactions and edge cases.
- Simulated different deposit, claim, and referral scenarios to assess functionality and uncover potential exploits.
- Focused on scenarios identified during the manual review and client concerns (e.g., infinite minting, reward calculation errors).
- Leveraged tools like Hardhat and Ganache to deploy and test the smart contract locally.
- Automated Testing:
- Employed static analysis tools like Slither to identify vulnerabilities through automated code scanning.
- Utilized symbolic execution tools like Mythril to explore various code execution paths and uncover potential attack vectors.
- Integrated unit tests are written by the CDP team to verify specific contract functions and their behaviour.
- Reporting & Remediation:
- Prepared a detailed report outlining all identified vulnerabilities, categorized by severity and potential impact.
- Provided clear recommendations for fixing each vulnerability, including code snippets and best practices.
- Collaborated with the CDP team to prioritize and address the identified issues.
- Conducted additional verification testing after vulnerability fixes were implemented.
QuillAudits' Strategic Approach to CDP Security Audits
We prioritize threat modeling based on platform-specific risks. Security-first, we identify and mitigate vulnerabilities beyond functionality testing. Using white-box and black-box tests, we conduct thorough vulnerability assessments. Maintaining transparency, we communicate openly with the CDP team. Emphasizing clarity, we present actionable insights for efficient issue resolution.
Comprehensive Audit Discoveries and Remediation Strategies
Throughout the audit process, we unearthed a total of 33 issues, spanning from minor concerns to critical vulnerabilities. Among these, some of the critical issues identified were: Here's how we remediated them :
- Unauthorized Claim/ Compound:
- Users could claim/compound a substantial amount without making a deposit or waiting for the stipulated time.
- Precision Loss in mintCDP():
- Precision loss and unscaled values were identified while calculating rewardPerShare in the mintCDP() function.
- Multiplication Accuracy:
- Multiplication operations were prone to providing incorrect answers due to unscaled values, posing a potential risk to accurate calculations.
- Incorrect Share Allocation:
- The protocol was allocating shares for all days, even when there were no corresponding deposits, leading to inefficient use of resources.
- Logic Error in Referral Handling:
- Users could claim/compound a A logic error resulted in users always having their user.referral set to address(0), which could be exploited to trick the referral system. amount without making a deposit or waiting for the stipulated time.
- Referral Exploitation:
- Users could exploit the referral system to extract more CDP from the protocol, undermining its integrity.
Remediation & Impact:
All identified vulnerabilities were addressed by the CDP team, significantly enhancing the smart contract's security posture. Key improvements include:
- Implementation of reentrancy protection mechanisms.
- Accurate handling of decimal values using established libraries or best practices.
- Revised calculations with proper scaling factors.
- Fixing logic errors to ensure deposits and waiting periods are enforced.
- Addressing referral system vulnerabilities to prevent abuse.
CDP smart contract audit revealed and fixed critical vulnerabilities, safeguarding funds and ensuring platform stability. This underscores the need for proactive security in blockchain projects, crucial for financial asset management. Through audits and issue resolution, CDP reinforces platform security, bolstering user trust.




