
Before QuillAudits
- Security concerns about potential vulnerabilities in core contracts, including re-entrancy attacks and business logic issues.
- Smart contracts like BukNFTs, BukPosNFT, BukProtocol, BukRoyalties, BukTreasury, MarketPlace, SignatureVerifier, and Token contracts were not fully tested.
- Critical vulnerabilities included unrestricted booking, potential NFT misuse, and inconsistent transaction logic.
- Functions like bookRooms(), checkout(), and emergencyCancellation() had flaws causing financial and operational issues.
After QuillAudits
- Implemented re-entrancy guards and verified ownership in transactions, ensuring consistency in business logic to prevent misdirected funds and operational inconsistencies.
- Performed a detailed line-by-line code review, developed and executed extensive test cases, and used static and symbolic analysis tools to identify and address vulnerabilities in the contracts.
- Implemented validation checks in bookRooms(), enhanced mintBukNFT() to validate before minting, revised checkout() to verify bukNFT ownership, aligned emergencyCancellation() and cancelRooms() to direct cancellation charges to the correct addresses.
- Refined bookRooms() for secure bookings, enhanced checkout() to verify NFT ownership, and aligned emergencyCancellation() for transferring charges to the intended destination.
Get an Audit done today for your Smart Contract
Join 1400+ leaders who secured themselves from losing Billion Dollars


Buk Protocol offers a modular infrastructure for dApps and marketplaces, enabling the tokenization and on-chain trading of dynamic assets. This omni-chain system includes an inventory aggregation layer and provides APIs, SDKs, widgets, and open-source libraries for creating secondary markets.
Buk Protocol is Redefining Dynamic Asset Management
Buk Protocol is a multichain blockchain platform (currently deployed on Polygon) designed to create secondary markets for all assets that expire such as limited-time gaming collectibles, hotel and airline reservations, events & concert passes, and much more. These assets typically lose value after use or expiration, but Buk Protocol transforms them into tradable assets on the blockchain. It provides a modular infrastructure for dApps and marketplaces, featuring an omni-chain inventory aggregation layer. Powered by the $BUK token, it supports fee payments, governance, and incentivization, and also offers tools like APIs, SDKs, widgets, and open-source code libraries for builders and existing web3 marketplaces to create secondary markets of dynamic assets.
Addressing Buk Protocol’s Re-Entrancy & Business Logic Security Concerns
The Buk Protocol faces critical challenges, notably the risk of re-entrancy attacks that exploit vulnerabilities in their smart contracts, potentially compromising transaction integrity and fund security. Additionally, they showed concerns regarding business logic vulnerabilities across core contracts like Bukprotocol, Treasury, Buk NFT, and Marketplace. These vulnerabilities could lead to issues such as improper asset ownership handling or inconsistent transaction logic. Addressing these concerns requires thorough auditing and proactive measures to strengthen contract security and ensure reliable platform functionality, thereby safeguarding user assets and maintaining operational trust.
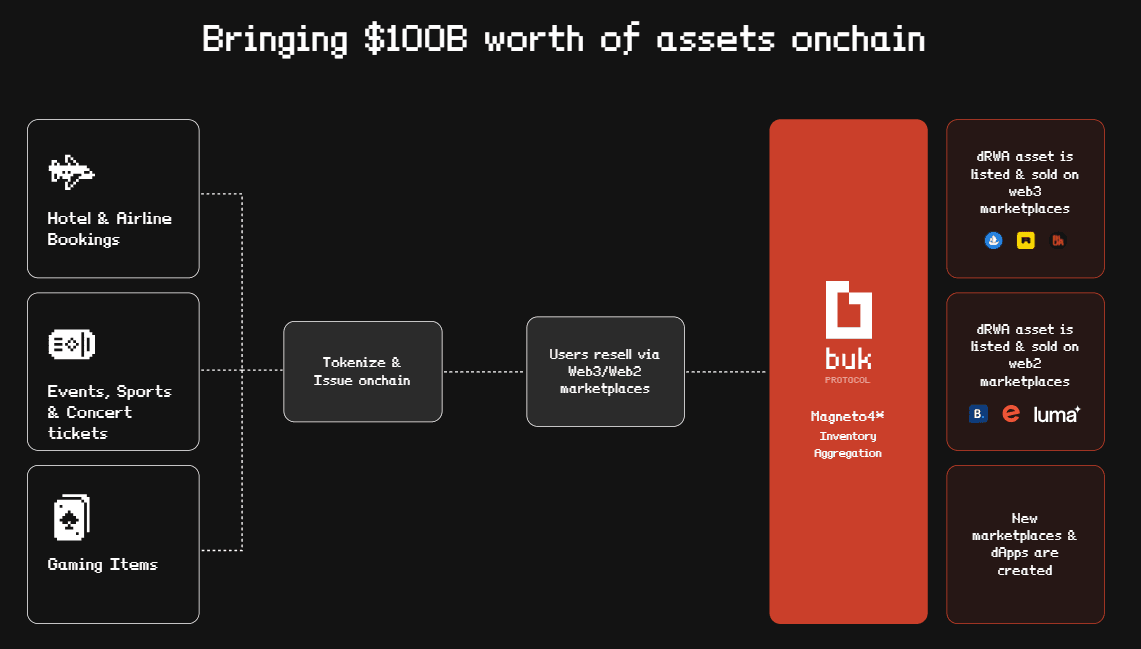
Buk Protocol’s Journey Through Our Audit Process
- Information Gathering:
- Collected and reviewed all relevant documentation, including whitepaper, technical specifications, and design documents.
- Obtained a clear understanding of the BukProtocol platform's functionality and intended user interactions.
- Discussed client concerns and specific areas of focus for the audit.
- Manual Code Review:
- Conducted a line-by-line review of the smart contract code, focusing on:
- Vulnerability identification: Searching for known vulnerabilities like reentrancy, front-running, integer overflows, and access control issues, etc.
- Logic flaws: Identifying inconsistencies or unintended behaviors in the code logic.
- Solidity best practices: Compliance with secure coding standards and adherence to established guidelines.
- Conducted a line-by-line review of the smart contract code, focusing on:
- Functional Testing:
- Developed and executed a comprehensive set of test cases covering various user interactions and edge cases.
- Leveraged tools like Hardhat and Ganache to deploy and test the smart contract locally.
- Automated Testing:
- Employed static analysis tools like QuillShield to identify vulnerabilities through automated code scanning.
- Utilized symbolic execution tools like Mythril to explore various code execution paths and uncover potential attack vectors.
- Integrated unit tests are written by the Buk team to verify specific contract functions and their behaviour.
- Reporting & Remediation:
- Prepared a detailed report outlining all identified vulnerabilities, categorized by severity and potential impact.
- Provided clear recommendations for fixing each vulnerability, including code snippets and best practices.
- Collaborated with the Buk Protocol team to prioritize and address the identified issues.
- Conducted additional verification testing after vulnerability fixes were implemented.
QuillAudits Strategic Approach to Buk Protocol’s Security Audits
Our methodology for Buk Protocol Smart Contracts combines threat modeling, a security-first mindset, and comprehensive testing, including both white-box and black-box methods. We emphasize transparency and clear communication with the Buk Protocol team, providing actionable insights and detailed recommendations for swift vulnerability resolution, and ensuring a robust security posture.
Comprehensive Audit Discoveries and Remediation Strategies
Our thorough and extensive audit uncovered 2 critical vulnerabilities, 2 Medium-severity issues, and 1 Low and 3 informational findings.
Here is a breakdown of the critical vulnerabilities in audit discoveries and remediation strategies:
Audit Discoveries:
- Unrestricted Booking and Potential NFT Misuse:
- Discovery: QuillAudits identified a critical vulnerability in the
bookRooms()function of BukProtocol.sol, where bookings could be made with a price of zero. This oversight allowed attackers to exploit the system by booking rooms without paying the intended price and later listing it to some other marketplace for a much higher price. - Impact: This vulnerability posed several risks:
- Financial Loss: Unrestricted free bookings could lead to lost revenue for Buk Protocol, impacting its financial sustainability.
- Market Manipulation: Malicious actors could mint NFTs associated with unvalidated bookings and sell them on secondary marketplaces, potentially manipulating prices and harming market integrity.
- Reputational Damage: Users might lose trust in Buk Protocol if they were unable to claim their booked rooms due to fraudulent activities.
- Discovery: QuillAudits identified a critical vulnerability in the
- Inconsistent NFT Ownership Handling:
- Discovery: During the audit, the QuillAudits team found inconsistencies in the
checkout()function of BukProtocol.sol regarding the handling of NFT ownership. The function attempted to burn bukNFTs and mint new bukPOSNFTs without verifying if the function caller was the current owner of the bukNFT. - Impact: This flaw could lead to:
- Transaction Reversion: If the current owner of the bukNFT had transferred it before the checkout process was completed, the burn operation would fail, potentially causing transaction reversion and disrupting user transactions.
- User Experience Issues: Inconsistent NFT handling could lead to frustration among users who expected smooth and reliable transactions on the platform.
- Discovery: During the audit, the QuillAudits team found inconsistencies in the
- Inconsistent Transaction Logic:
- Discovery: QuillAudits identified inconsistencies in the transaction logic of the
emergencyCancellation()function in BukProtocol.sol. The function routed cancellation charges to _bukTreasury instead of _bukWallet, contrary to the intended behavior specified in thecancelRooms()function. - Impact: This discrepancy could result in:
- Misdirected Funds: Cancellation charges meant for _bukWallet could be incorrectly directed to _bukTreasury, disrupting the financial flow and potentially impacting budgeting and revenue tracking for Buk Protocol.
- Operational Inconsistencies: The conflicting transaction logic between
emergencyCancellation()andcancelRooms()could create confusion within the platform's internal operations.
- Discovery: QuillAudits identified inconsistencies in the transaction logic of the
Remediation Strategies:
1. Unrestricted Booking and Potential NFT Misuse:
- QuillAudits implemented comprehensive validation checks within the `bookRooms()` function to enforce proper booking price validation. The updated function now verifies if the booking price is correct before processing the booking.
- The `mintBukNFT()` function was enhanced to validate booking details before minting NFTs. This ensures that NFTs are only minted for legitimate bookings.
2. Inconsistent NFT Ownership Handling:
- To address the inconsistency in NFT ownership handling, QuillAudits revised the `checkout()` function. The updated function now includes a verification step to ensure that the function caller is the current owner of the bukNFT before proceeding with the burn and mint new bukPOSNFT.
3. Inconsistent Transaction Logic:
- QuillAudits aligned the transaction logic between `emergencyCancellation()` and `cancelRooms()` functions to ensure consistent routing of cancellation charges.
- Cancellation charges are now directed according to the intended behavior specified in the `cancelRooms()` function, with charges routed to _bukWallet and not _bukTreasury.
Impressed by our findings and recommendations, the Buk Protocol developers **promptly addressed all identified vulnerabilities**. Through our collaborative efforts, the Buk Protocol project is now **significantly more secure**, ensuring the protection of user funds.
The Buk Protocol's smart contract security audit identified and resolved critical vulnerabilities, safeguarding user funds and ensuring platform stability. This case study highlights the importance of proactive security measures for blockchain projects, particularly those involving financial assets. By conducting thorough audits and addressing the issues found, the Buk Protocol team has taken a significant step towards securing its platform and safeguarding user trust.




