StarkNet is a layer-2 scaling solution for Ethereum that aims to improve the scalability, privacy, and usability of Ethereum-based decentralised applications (dApps). StarkWare, a blockchain technology company that specialises in zero-knowledge proof (ZKP) systems, is developing it.
StarkNet uses a technology known as Validium, which enables dApps to run off-chain while maintaining the security of the Ethereum mainnet. This means that dApps can benefit from the scalability and transaction throughput of off-chain computation while maintaining the Ethereum network's security and trustworthiness. Furthermore, StarkNet supports privacy-preserving computations via the use of ZKPs, allowing dApps to protect sensitive user data while still providing a transparent and auditable system.
Cairo, a low-level programming language that can be used to write StarkNet-specific code, is provided by StarkNet as a development kit. Cairo is optimised for zero-knowledge proofs (ZKPs) and is intended to provide a high level of flexibility and efficiency for building complex StarkNet applications.
Why Cairo Smart contracts Need Security Audit?
Smart contracts, like any other software application, are vulnerable to a variety of security issues that can jeopardise their security, reliability, and performance.
Conducting a thorough security audit is one of the most important steps in developing secure and reliable smart contracts. Security audits are critical for identifying and mitigating potential vulnerabilities and ensuring that smart contracts written in Cairo for StarkNet function as intended.
Some of the most common vulnerabilities that can affect Cairo smart contracts
Cairo Smart Contract Vulnerabilities:
- Reentrancy attacks: where an attacker exploits a vulnerability in the contract code that allows them to repeatedly call the same function before it has completed executing, leading to the loss of funds.
- Front-running attacks: where an attacker exploits a time delay in the execution of transactions to their advantage, by executing a similar transaction with a higher fee, resulting in a loss of profits or funds for the victim
- Time manipulation: where an attacker manipulates the time on a smart contract to execute a function at an unintended time, leading to a loss of funds or other unintended consequences.
- Malicious libraries: where a smart contract uses external libraries that have vulnerabilities or are malicious, leading to a potential loss of control of the contract or funds.
- Logic errors: These are bugs in the code that allow attackers to exploit unexpected smart contract behaviour. For example, an error in a conditional statement could allow an attacker to circumvent certain checks and balances.
- Reentrancy attacks: occur when an attacker repeatedly invokes a function in a smart contract before the previous invocation has been completed, resulting in unexpected behaviour or even financial losses.
- Overflows and underflows: integers occur when an arithmetic operation produces a number too large or too small to be stored in the available memory. Attackers can use these flaws to manipulate the state of the smart contract.
- Input validation issues: Issues with input validation occur when the smart contract fails to validate user input properly. Attackers can use these flaws to provide malicious input, jeopardising the smart contract's security.
- Insufficient Access Controls: Inadequate access control: These flaws occur when the smart contract properly restricts access to specific functions or data. Attackers can use these flaws to gain unauthorised access to the smart contract.
To mitigate these vulnerabilities, performing thorough security audits on Cairo-written smart contracts before deploying them to production is critical.
Cairo Smart Contract Audit Process
Things We Cover in the Audit Process :
- Business Logic’s Review
- Functionality Checks
- Access Control & Authorization
- Escrow manipulation
- Token Supply manipulation
- User Balances manipulation
- Data Consistency manipulation
- Kill-Switch Mechanism
- Operation Trails & Event Generation
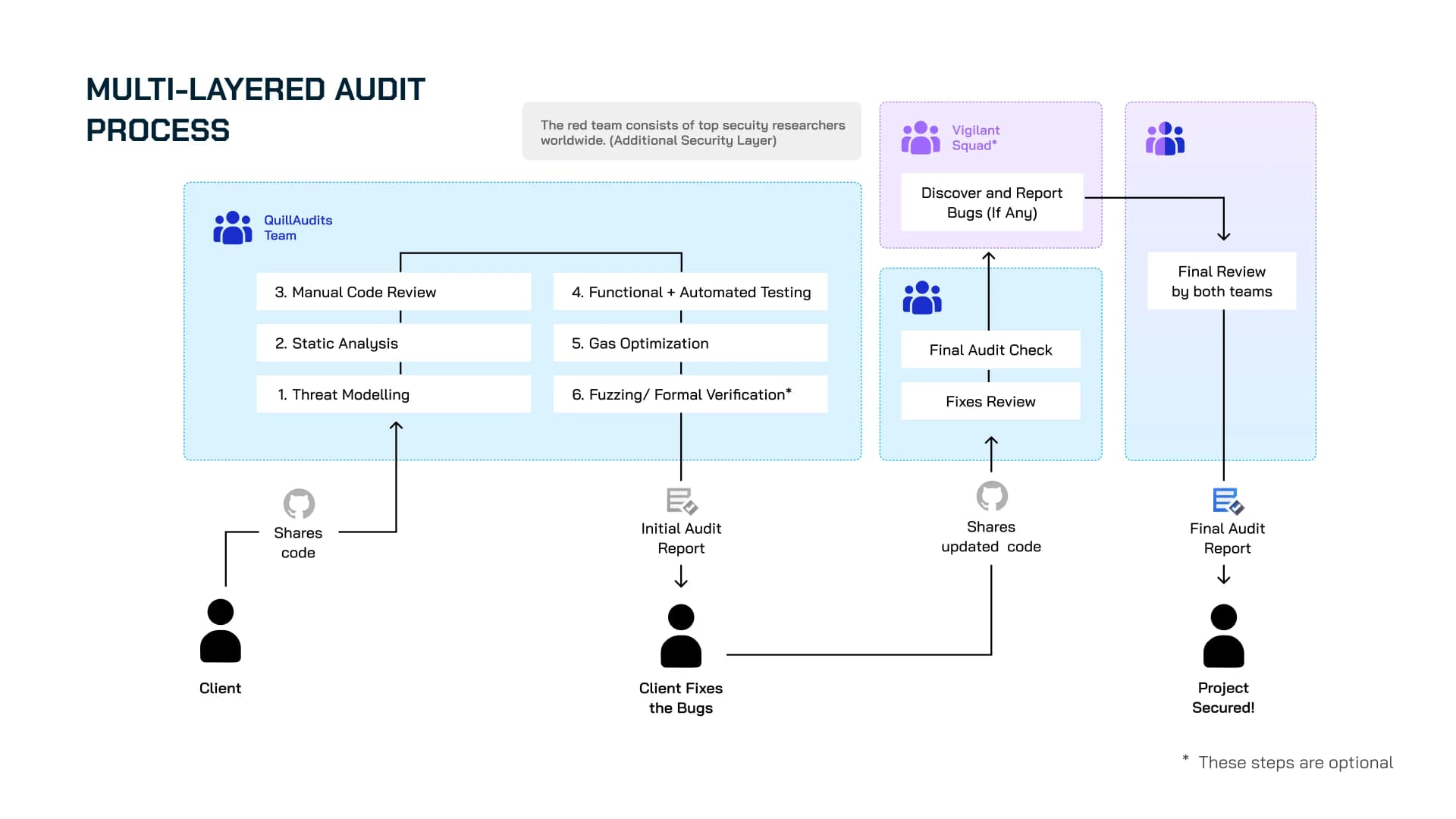
We ensure your smart contract goes through all the stages, from manual code review to automated testing, before generating the Initial Audit Report. Once your team updates the code, we thoroughly scrutinise the smart contract to provide you with the Final Audit Report. Lets's dive deep into it and explore more.
Step 1 - Specification Gathering / Prepare For a Security Audit
The first step is to gather all the necessary information and prepare for a security audit. This stage is crucial for the success of the audit, and here is how you can prepare for it:
- Code quality: Ensure code quality by removing dead code and comments, following the Solidity / Rust (Solana) style guide, and using comments to document complex parts of the code. Test the code by performing high coverage and high-quality unit tests, ensuring the contracts can be compiled and fully tested.
- Code freeze: Freeze the code, specify the commit hash, or deploy the code on testnet and share the link. After freezing the code, gather the specifications from the development team to know the intended behaviour of the smart contract through the 'Smart Contract Specification' document.
Step 2 - Manual Review
Manual review is a critical step that involves looking for undefined, unexpected behaviour and a Wide Variety of security vulnerabilities. The following aims are considered during the manual review:
- Focus on security issues, attacks, mathematical errors, logical issues, etc.
- Check the code for vulnerabilities that can be exploited.
- Verify that every detail in the specification is implemented in the smart contract.
- Verify that the contract does not have any behaviour that is not specified in the specifications.
- Verify that the contract does not violate the originally intended behaviour of specifications.
Step 3 - Testing over the Latest Attack Vectors
The QuillAudits researches newly discovered attacks and tries to replicate them to ensure the project is safe from those attacks. Attack vectors could include:
- Re-Entrancy
- Exposing unwanted external functions
- View Functions that modify the state
- Missing Pausing functionality
- Signature Replay Attacks
- Storage Variable Name Clashing
- Interacting with Arbitrary Tokens
- Missing Zero Address Checks
- Missing Zero Value Checks
- Toolchain and Best Practices
- Use standard and/or reputable and tested libraries
- Use up-to-date Cairo versions
- Upgradable Contracts
- Deployment check of your implementation contract
- Oracles
- Price Feeds
- Pseudo Random Number Generators
- Logic Flaws
- Frontrunning
- Governance Attacks
- Denial of Service (DoS)
Step 4 - Functional Testing
In this step, the smart contract will be manually deployed in a sandbox environment, and smart contract functions will be tested on multiple parameters and under multiple conditions.
This phase is intended to verify the intended behaviour of the smart contract and ensure that smart contract functions are not consuming unnecessary gas. Gas limits of functions will be verified in this stage.
Step 5 - Automated Tool Testing
Tool We Use
ProtostarNilePytestStarknet-devnetStarkNetApe WorxStarknet-py
Step 6 - Initial Audit Report
QuillAudits provide the project team with a comprehensive report called the Initial Audit Report (IAR). The report will contain details of the audit and Recommendations for any vulnerabilities in the smart contract.
The development team is expected to resolve the identified bugs & make suitable changes to the code. If necessary, the Quillaudits will connect with development partners for issues fixing.
How can you help?
You have to prepare an 'Updation Summary' or 'Comment Report' carrying details of the changes you've made after getting the IAR; this would help us identify the changes and test them rigorously.
Step 7 - Final Audit Report
After initial audit fixes, the process is repeated, and the Final Audit Report is delivered. Even after your fixes, some issues are still unresolved, and/or those changes have led to a few more issues.
So, after receiving the Final Audit report, you have to take a call (based on the severity table containing the unresolved issues) on whether to alter the code again or to move forward as it is.
Step 8: Quill Vigilant Squad*
Following the completion of the second audit review, the Fixed codebase, along with the comprehensive audit report, will be formally delivered to our dedicated Vigilant Squad. This elite team is comprised of world-class security researchers, each possessing extensive experience and expertise in identifying and analyzing vulnerabilities within complex systems. The Vigilant Squad will undertake a meticulous and in-depth review of both the codebase itself and the accompanying report. They will dedicate their full time and resources to this critical task, leveraging their specialized skills to proactively search for and uncover any potential security issues, however subtle they may be. In the event that the Vigilant Squad discovers any vulnerability, security flaw, or other issue, we will be notified immediately, ensuring swift action can be taken to mitigate any potential risks.
How you can help - You have to prepare an 'Updation Summary' or 'Comment Report' with details of the changes in case, if you get any New issues from our side; this would help us identify the differences and test them rigorously.
Step 9 - Delivery
After getting a green light from the previous step, we send the report to our designers. With their skills, they make a PDF version of the Audit Report and beautifully showcase everything.
The report then gets uploaded onto our official GitHub Repository. We then share the link to the Audit Report and a Certificate of Compliance from QuillAudits.
Step 10: Post-Audit
After the Final Audit report, we take your project in front of the masses through :
Social Media Announcements
- As per your requests from you, we make an audit announcement from our social media handles to mark the completion of the Audit.
LinkedIn - X (Twitter) - Telegram - Reddit - Medium

The completion of this step totally depends on the calendar availability of our Marketing Team. Therefore, this step might take some time to complete.
- Access to QuillAudits Ecosystem (Exchanges, IDO, KYC, Incubators, VC Partners)
AMA Sessions
- Expert auditors explain the nuances of the Audit Report.
- Q&A and direct interaction with your audience to build trust in your project.
Niche Targeted PR Services
- Articles & guest posts in renowned publications.
- Cross-platform promotions to give more exposure to the project.
Organize Product Launches, Community Meetups, etc.
- QuillAudits team will help you in your product launch in India.
- Set up community meetups, product workshops and web3 events for you.
- QuillAudits expert team and partners will handle everything from content creation to marketing and event location to event coordination.
What Can the Project Team Expect From Us?
- Delivery of initial report within the agreed timeline (considering a margin of ±2 days due to unforeseen circumstances)
- Reviewing the final version of the code before concluding the audit.
- Following the complete audit process, i.e., Manual Review, Functional Testing, Automated Testing, and Reporting bug findings.
- Publishing Audit Reports and making post-audit announcements based on agreed-upon terms.
What Do We Expect From the Project Team?
- A working test suite (all tests written are executable) covering at least 90% of the project code and edge-case scenarios.
- Structured code following reasonable naming conventions and consistent coding style.
- Well-documented contracts/functions and updated whitepaper.
- Fixing issues from the initial bug-finding report and providing detailed comments, stating what fixes have been implemented to the concerned issues.
- Reviewing the final report so that QuillAudits can conclude the audit.