Things We Cover in Audit Process
- Business Logics Review
- Functionality Checks
- Access Control & Authorization
- Signer authorization
- Account data matching
- Sysvar address checking
- Owner checks
- Type cosplay
- Initialization
- Arbitrary cpi
- Duplicate mutable accounts
- Bump seed canonicalization
- PDA Sharing
- Incorrect closing accounts
- Missing rent exemption checks
- Arithmetic overflows/underflows
- Numerical precision errors
- Solana account confusions
- Casting truncation
- Insufficient SPL token account verification
- Signed invocation of unverified programs
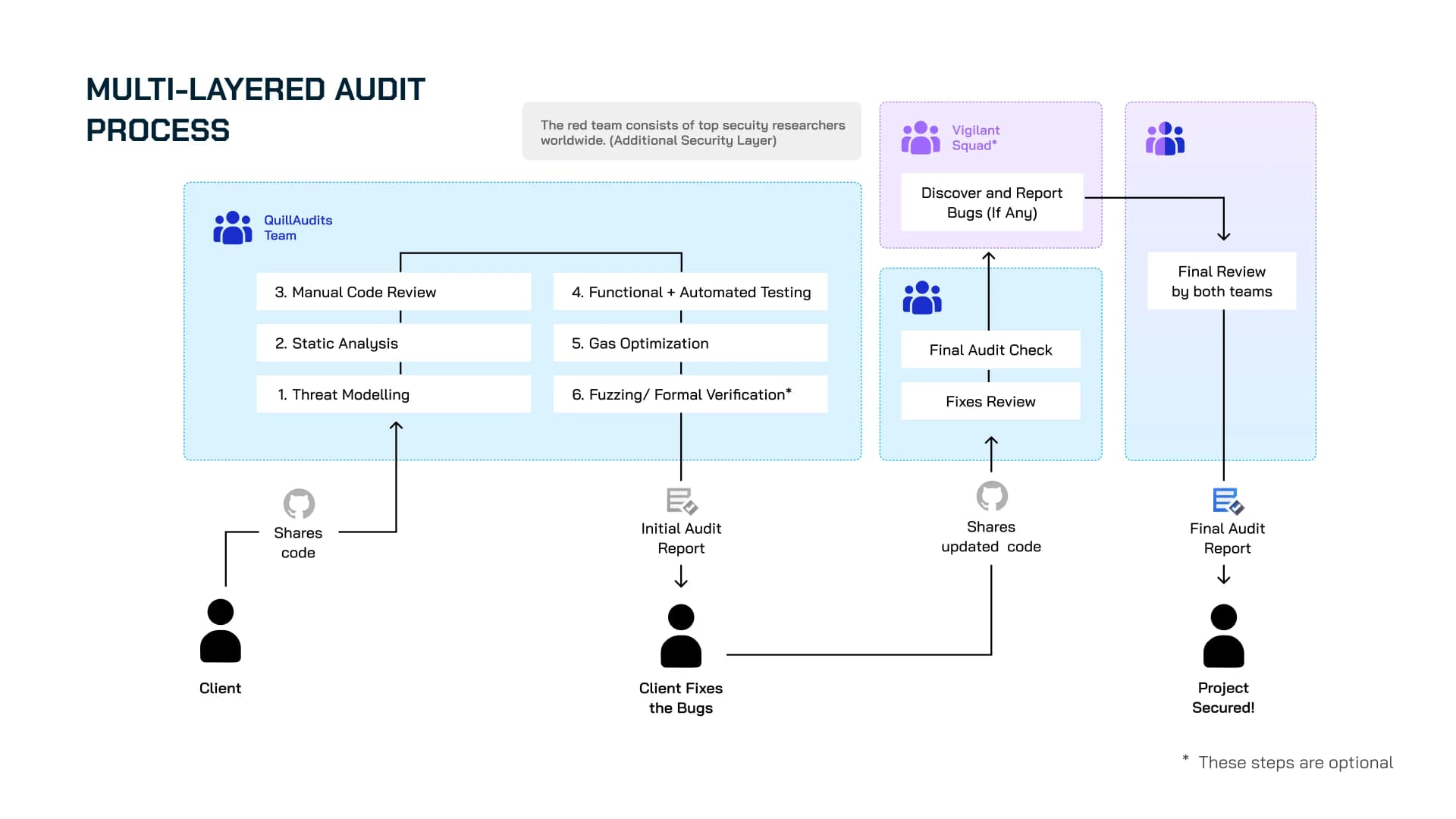
We ensure your smart contract goes through all the stages, from manual code review to automated testing, before generating the Initial Audit Report. Once your team updates the code, we do a thorough scrutiny of the smart contract to provide you with the Final Audit Report. Let's dive deep into it and explore more.
Multi-Layer Audit Process
Step 1 - Specification Gathering / Prepare For a Security Audit
This is the most crucial stage because the detail is key for a successful smart contract Security audit. Here is how you can prepare for it:
Code quality
- Remove dead code and comments
- Consistent coding style
- Follow the Rust (Solana) style guide
Use comments to document complex parts of the code but also make sure these are. consistent with the code
Test the code
- Make sure the contracts can be compiled and fully tested
- Perform high coverage and high-quality unit tests
This will maximize focus on the difficult parts of the code. Auditing should not be discovered that some functions are un-callable, or do not do what they are expected to do under entirely straightforward inputs. Optimal auditing should focus on unexpected, corner-case, possibly adversarial behavior.
Code freeze
- Freeze the code and specify the commit hash. Or, deploy the code on testnet and share the link.
After freezing the code, we will gather the specifications from you to know the intended behavior of the smart contract through the 'Smart Contract Specification' document.
How you can help - Please ask your developers to fill the specification doc - It would help us to understand & verify the business logic, and facilitate confirming everything thoroughly.
Step 2 - Manual Code Review
Here we would look for undefined, unexpected behavior and common security vulnerabilities. The goal is to get to as many skilled eyes on contract code as possible. Aims of manual review:
- Focus on issues regarding security, attacks, mathematical errors, logical issues, etc.
- Check the code for any vulnerabilities that can be exploited.
- Verify that every detail in the specification is implemented in the smart contract.
- Verify that the contract does not have any behavior that is not specified in specifications.
- Verify that the contract does not violate the original intended behavior of specifications.
- The smart contract will be manually deployed locally in a local cluster.
- All the transaction hashes will be recorded.
- Accessibility of the accounts’ data in a secure manner by the programs.
- Determining the user-controlled parameters where arbitrary data could be passed.
Step 3 - Functionality Testing
- Smart contract functions will be unit tested on multiple parameters and under multiple conditions to ensure that all paths of functions are functioning as intended.
- In this phase, the intended behavior of the smart contract is verified.
- In this phase, the total accounts(data) needed for a program are verified and tested.
- We also verify the data in accounts that will be fetched by the Solana programs.
- Tests are conducted in either Typescript or JavaScript to make sure that bugs related to syntax misunderstandings are coverable with tests and not just replicated in tests.
Step 4 - Testing over Latest Attack Vectors
- Team researches over newly discovered attacks(like market manipulation, LP pricing, front running vectors, and more), and try to replicate them on the project in order to make sure, the project is safe from those attacks
- In case, if the current implementation is found to be vulnerable to some of the newly discovered attacks, we provide a recommendation to the developer team so that they can patch the vulnerability in an efficient manner without any (or with some) changes in the code’s logic.
We provide testing on the following attack vectors as well:
- Replay Vulnerability
- Re-entrancy
- Integer Overflow and Underflow Vulnerability
- Arithmetic Accuracy Deviation Audit
- Arbitrary signed program invocation
- Solana account confusions
- Missing signer check
- Unsafe External Call
- Design Logic
- unsafe Rust Code
- outdated Dependencies
- Scoping and Declarations
- Arithmetic Accuracy Deviation
Step 5 - Testing with Automated Tools
Testing with automated tools is important to catch those bugs that humans miss. We also implement techniques like fuzzing to ensure that we may articulate real-world attack vectors as much as possible. Some of the tools we would use are:
- cargo-audit
- Soteria
- cargo-clippy
- cargo-tarpaulin
- cargo-geiger
Step 6 - Initial Audit Report
In the end, we would provide you with a comprehensive report, which we call the Initial Audit Report (IAR):
How you can help - You have to prepare an 'Updation Summary' or 'Comment Report' carrying details of the changes you've made after getting the IAR; this would help us identify the changes and test them rigorously.
- A Comprehensive Audit report.
- Encapsulates details of the Audit & solutions to the vulnerabilities (if we found any) in your contracts.
- We expect you to resolve the identified bugs & make suitable changes to the code.
Note - Please acknowledge that once the Audit Scope is frozen ( commit hash or explorer link ), we start the Audit Process. In case, you make any changes to the code in-between the process, we will be able to check the updated code only after delivering the Initial Audit Report. We cannot abort the process in between and start working on the updated code.
Step 7 - Final Audit Report
After initial audit fixes, the process is repeated, and the Final Audit Report is delivered. There is a possibility that even after the fixes you've made, some issues are still not resolved, and/or those changes have led to a few more issues.
So, after receiving the Final Audit report, you have to take a call (based on the severity table containing the unresolved issues) whether to alter the code again or to move forward as it is.
Step 8: Quill Vigilant Squad*
Following the completion of the second audit review, the Fixed codebase, along with the comprehensive audit report, will be formally delivered to our dedicated Vigilant Squad. This elite team is comprised of world-class security researchers, each possessing extensive experience and expertise in identifying and analyzing vulnerabilities within complex systems. The Vigilant Squad will undertake a meticulous and in-depth review of both the codebase itself and the accompanying report. They will dedicate their full time and resources to this critical task, leveraging their specialized skills to proactively search for and uncover any potential security issues, however subtle they may be. In the event that the Vigilant Squad discovers any vulnerability, security flaw, or other issue, we will be notified immediately, ensuring swift action can be taken to mitigate any potential risks.
How you can help - You have to prepare an 'Updation Summary' or 'Comment Report' with details of the changes in case, if you get any New issues from our side; this would help us identify the differences and test them rigorously.
Step 9 - Delivery
After getting a green light from the previous step, we send the report to our designers. With their skills, they make a PDF Version of the Audit Report and beautifully showcase everything in it.
Sample Audit Report 1 - NovaDex
Sample Audit Report 2 - EnRex (April 2022)
Sample Audit Report 3 - EnRex (March 2022)
The report then gets uploaded onto our official GitHub Repository. We then share with you the link to the Audit Report along with a certificate of Compliance from QuillAudits.
Post-Audit-Announcements
- As per your requests, we make an Audit Announcement from our social media handles to mark the completion of the Audit.
- Access to QuillAudits Ecosystem (Exchanges, IDO, KYC, Incubators, VC Partners)

The completion of this step totally depends on the calendar availability of our Marketing Team. Therefore, this step might take some time to complete.
AMA Sessions
- Expert Auditors Explaining the Nuances of the Audit Report
- QnA and Direct Interaction with Your Audience to Build Trust in Your Project
Niche Targeted Marketing/PR Services
- Articles & Guest Posts in Renowned Publications
- Cross-Platform Promotions to Give More Exposure to the Project
Organize Product launches, Community Meetups etc
- QuillAudits team will help you in your product launch in India.
- Set up community meetups, product workshops and web3 events for you.
- QuillAudits expert team and partners will take care of everything from content creation to marketing and event location to event coordination.
What can the Project Team Expects from Us?
- Delivery of initial report within the agreed timeline (considering a margin of +- 2 days due to unforeseen circumstances)
- Reviewing the final version of the code before concluding the audit
- Following the complete audit process, i.e., Manual Review, Functional Testing, Automated Testing, and Reporting bug findings.
- Publishing Audit Reports and Making Post Audit Announcements based on agreed-upon terms
What do We expect from Project Team?
- A working test suite(all tests written are executable) covering at least 90% of the project code and edge-case scenarios.
- Structured code following reasonable naming conventions and consistent coding style.
- Well-documented contracts/functions and updated whitepaper
- Fixing issues from the initial bug-finding report and providing detailed comments, stating what fixes have been implemented to the concerned issues.
- Reviewing the final report so that QuillAudits can conclude the audit
Feedbacks
Your feedback helps us to improve and enhance. It helps us inculcate innovations in our services to improve and serve you better.
Please click here to provide your valuable feedback - Feedback Link
Survey - Kindly provide your valuable inputs by filling out the survey form to aid us in understanding the current DeFi & NFT market better. It would help us to improve upon our methodology for 𝘀𝗺𝗮𝗿𝘁 𝗰𝗼𝗻𝘁𝗿𝗮𝗰𝘁𝘀 𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 - Survey Link
About us
QuillAudits is a leading blockchain security firm with 7 years of experience, securing $30B in TVL with multi-layered audit framework, across 1400+ projects in DeFi, GameFi, NFT, Gaming, and all blockchain layers.
Our senior auditors conduct line-by-line code reviews, combining manual & AI-driven audits for smart contracts on 20+ chains including Ethereum, BSC, Arbitrum, Algorand, Tron, Polygon, Polkadot, Fantom, NEAR, & Solana. We also offer token risk assessments & real-time monitoring tools to fortify Web3 security.
Beyond audits, we’ve hosted 50+ global events and 300+ workshops to educate and support the Web3 community.

Connecting with you - By this time, you must have been added to a closed group with the Auditing Team. You would be connected with the Project Manager and the Auditors through this dedicated channel during the process for collaboration and instant resolution. At any point, if you face any query or find a need to discuss anything - we are just a message away!