Every time a major exploit shakes the Web3 space, one question echoes through the industry: "Didn’t they get an audit?"
The assumption is simple, if a project has been audited, it should be secure.
Yet, time and again, vulnerabilities slip through, leading to catastrophic losses.
Why?
Why Are Hacks Still Happening Despite Smart Contract Audits?
The reality is that traditional smart contract Audits often follow a one-dimensional approach: run automated tools, do a surface-level manual review, generate a report, and move on.
This leaves projects exposed to hidden vulnerabilities that automated scanners simply can’t catch.
Security isn’t about checking boxes, it’s about resilience.
And that’s why we are introducing the Multi-Layered Audit Framework, designed to stress-test projects from every possible angle before attackers can exploit them.
What is the Multi-Layered Audit Framework?
The Multi-Layered Audit Framework is a holistic security approach that combines manual expertise, automated testing, and independent verification.
Instead of relying on a single review process, this framework stacks multiple layers of validation to ensure that vulnerabilities are identified and addressed comprehensively.
Key Components of the Framework
1. Deep-Dive Requirement Gathering:
Before the actual Smart contract audit process begins, an extensive discovery phase is conducted.
This involves:
- Understanding the architecture of the smart contract or blockchain application.
- Identifying external dependencies, oracles, third-party integrations, and interactions with other protocols.
- Mapping out the threat model, which helps smart contract auditors anticipate potential attack vectors specific to the protocol.
- Evaluating project documentation, whitepapers, and specifications to ensure the smart contract audit aligns with the intended functionality.
This phase ensures that the smart contract auditors are not just checking code for common vulnerabilities but are also context-aware, making their analysis far more insightful and precise.
2. Manual Code Review by Experienced Auditors
Automated tools are great for catching known vulnerabilities, but they often fall short when it comes to logical flaws or protocol-specific risks.
This is where manual review comes in, the first & most important part of the entire process:
- Security engineer/auditors with deep domain expertise analyze smart contracts for logical inconsistencies, reentrancy risks, and improper state transitions.
- They check for business logic vulnerabilities, ensuring that the protocol behaves as intended under various edge cases.
- Reviewers also assess the implementation of best practices, ensuring compliance with Solidity/EVM standards, gas efficiency optimizations, and secure key management.
By leveraging human intuition and expertise, this phase ensures that vulnerabilities beyond automated detection are identified and addressed.
3. Automated Testing
Once the manual review is complete, the next layer involves automated tools that provide additional coverage by stress-testing the code.
This includes:
- Static analysis to detect reentrancy vulnerabilities, integer overflows, and unchecked external calls.
- Fuzz testing, which involves bombarding the contract with a variety of randomized inputs to identify unintended behaviors.
- Symbolic execution and formal verification, ensuring that functions always behave as expected under all possible execution paths.
- Unit testing & integration testing, simulating real-world attack scenarios to verify contract robustness.
These automated techniques act as a secondary safeguard, catching security flaws that might have been overlooked during manual review.
4. Client Fixes & Remediation
After the initial smart contract audit phase, the development team is provided with a detailed audit report containing:
- A comprehensive list of vulnerabilities, categorized based on severity (critical, high, medium, low, informational).
- Actionable recommendations for fixing each issue.
- Best practices to follow for future development to prevent similar security risks.
Once the developers implement the necessary fixes, the smart contract auditors perform re-audits to ensure all vulnerabilities have been resolved without introducing new ones.
This iterative process ensures a higher security assurance level before deployment.

5. Independent Verification by the Vigilant Squad
One of the most unique aspects of this multi-layered framework is the inclusion of a global security research community, a Red Team of independent security experts.
This stage:
- Brings in external researchers to revalidate the smart contract audit findings and identify any missed vulnerabilities.
- Encourages crowdsourced security efforts, leveraging different attack methodologies beyond the original audit team’s approach.
- Validates that the recommended fixes are effective, ensuring that previous vulnerabilities have been properly mitigated.
This independent verification step serves as a double-checking mechanism, adding an extra layer of security before public deployment.
6. Final Consolidation & Post-Audit Support
Once the audit findings have been thoroughly reviewed and all fixes are validated, the final audit report is prepared. However, the security process doesn’t stop there:
- The audit team provides ongoing support for security monitoring and incident response.
- Bug bounty programs are often recommended as an additional measure to encourage ethical hackers to test the security of the smart contract.
- Some projects opt for continuous security monitoring, where real-time threat detection tools are integrated to detect anomalies post-deployment.
By offering post-audit security measures, this framework ensures that security doesn’t end with the audit but becomes an ongoing priority for the project.
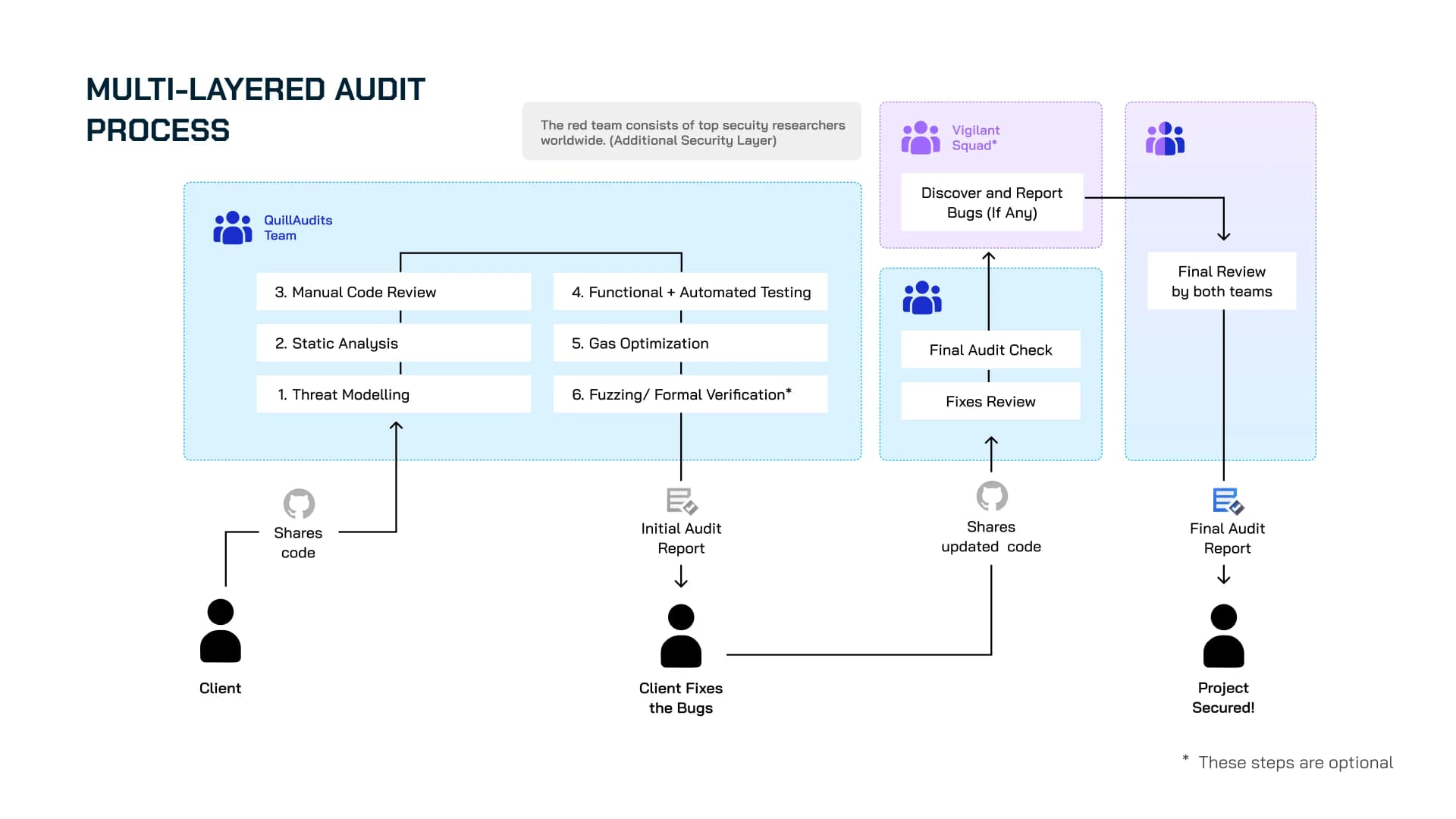
How Does the Multi-Layered Audit Framework Work?
The framework is structured to ensure each step builds upon the previous one, progressively tightening security. Here’s how it works:
1. Initial Audit by QuillAudits Team
Before diving into the code, the first step is understanding the project’s architecture and potential security risks.
This ensures that the audit isn’t just about finding generic vulnerabilities but rather tailored to the specific needs of the project.
We start with an in-depth discussion with the project team to gather details on:
- System architecture – How the smart contract or protocol is structured, including modularity, dependencies, and interactions with external systems.
- External dependencies – Whether the project integrates with oracles, third-party libraries, Layer-2 scaling solutions, or other protocols.
- Security assumptions & threat models – Understanding what attack vectors are most relevant to the protocol and how assets are secured.
Once we have this foundational knowledge, the initial audit process kicks off with a combination of manual analysis and automated tools to uncover vulnerabilities at multiple levels.
Threat Modeling
Before scanning for vulnerabilities, we map out the potential attack surfaces based on the contract’s design. This includes:
- Identifying entry points for attackers – Are there functions anywhere in the entire code that can be exploited by external users or malicious insiders?
- Assessing privilege levels and access controls – Who has administrative rights, and can they be misused?
- Checking for external integrations – If the contract depends on an oracle, a bridge, or an external API, could that be a point of failure?
By defining the threat landscape early, the audit team can prioritize testing for real-world risks rather than just theoretical issues.
Static Analysis
Static analysis is the first layer of automated security testing, where we run the smart contract through advanced security tools like Mythril, Echidna, Slither, Quillshield etc. to detect common vulnerabilities.
These tools scan the code without executing it, identifying risks such as:
- Reentrancy attacks – Can an attacker repeatedly call a function before the contract updates its state?
- Integer overflows and underflows – Are there unchecked arithmetic operations that could lead to unexpected behavior?
- Unchecked external calls – Does the contract call an external address without verifying its authenticity?
- Access control flaws – Are certain functions exposed to the public that should be restricted?
- While automated tools are useful for catching low-hanging security flaws, they often miss logical vulnerabilities—which is why the next step is manual code review.
Manual Code Review
This is one of the most critical parts of the audit, where our team of experienced security researchers manually analyzes the contract line by line.
This process allows us to:
- Identify business logic flaws – Does the contract behave as intended under all conditions?
- Assess smart contract interactions – Are there unexpected dependencies that could introduce vulnerabilities?
- Verify implementation of best practices – Are the correct Solidity patterns and security mechanisms in place?
Unlike automated tools, human auditors can think like attackers, probing the contract for unintended behaviors that could lead to exploits.
Functional Testing
Once the contract has been reviewed for vulnerabilities, we conduct real-world simulations to test its behavior in a variety of scenarios.
This involves:
- Unit testing – Running predefined test cases to verify individual contract functions.
- Integration testing – Checking how the contract interacts with external protocols, multisig wallets, governance mechanisms, and Layer-2 networks.
- Simulation of edge cases – What happens if the contract receives invalid inputs or is subjected to high network congestion?
By mimicking real-world conditions, we can detect issues that may not be obvious through static analysis or manual review alone.
Fuzzing & Formal Verification (Optional)
For projects requiring an extra layer of security, we use advanced testing techniques such as:
- Fuzz Testing – Feeding the contract with randomized, unexpected, or extreme inputs to see if it breaks or behaves unpredictably.
- Formal Verification – Mathematically proving that the contract adheres to its intended behavior under all possible execution paths.
These techniques are particularly useful for DeFi protocols, stablecoins, and high-value smart contracts, where even a small logic flaw could lead to catastrophic consequences.
Gas Optimization & Best Practices Review
Security is the primary focus, but gas efficiency is also crucial for a smart contract’s usability.
We review:
- Loop structures and storage operations – Are they optimized to reduce gas costs?
- Redundant code and unnecessary state updates – Are there areas where gas usage can be reduced?
- Function visibility and modifiers – Are they correctly applied to avoid excessive execution costs?
Optimizing gas usage ensures that the contract remains cost-effective for users while maintaining security and functionality.
Finalizing the Initial Audit Findings
After completing all these steps, we compile a detailed report with:
- All identified vulnerabilities, categorized by severity (critical, high, medium, low).
- Recommended fixes for each issue.
- Code snippets and explanations to help the development team understand and implement the necessary changes.
This marks the end of the initial audit phase, after which the development team can proceed with fixing the vulnerabilities before the re-audit and final verification process.
2. Client Fixes & Code Remediation
Once the initial audit report is delivered, the client team works on fixing the identified vulnerabilities.
But unlike conventional audits, where fixes are often the final step, this framework adds another layer of validation.
3. Final Review by Quill Team
The fixed code is re-audited to verify whether vulnerabilities have been properly addressed. This includes:
- Fixes Review – Ensuring previous vulnerabilities are patched correctly.
- Final Audit Check – Reassessing the entire codebase for any missed issues.

4. Independent Review by the Vigilant Squad
Once the initial audit is complete, the project undergoes a second round of scrutiny by the Vigilant Squad, a team of independent security researchers.
Their role is to validate the findings from the primary audit and conduct a fresh security assessment to uncover any potential risks that may have been overlooked.
This phase ensures a well-rounded security evaluation by introducing diverse expertise and testing methodologies. The Vigilant Squad follows a structured approach:
- The team conducts a separate, unbiased analysis of the smart contract without referencing the initial audit findings. This prevents any confirmation bias and helps surface unique vulnerabilities.
- Beyond conventional auditing methods, the squad employs symbolic execution, dynamic analysis, and adversarial testing to identify weaknesses in the code’s logic, execution flow, and security posture.
- The review focuses on uncommon attack scenarios, including game-theoretic vulnerabilities, unintended protocol interactions, and complex on-chain dependencies that could be exploited.
- Any issues flagged during the initial audit are rechecked to confirm whether the applied fixes fully mitigate the risk and do not introduce new vulnerabilities.
By the end of this step, the security review is reinforced with multiple perspectives and methodologies, ensuring that every possible attack vector is assessed before the final report is delivered.
5. Final Consolidation & Report Delivery
Once both our internal audit team and the Vigilant Squad have completed their assessments, the findings are consolidated into the final security report.
At this stage, we ensure:
- All issues are addressed – No vulnerability is left unresolved.
- Risk is fully assessed – Clients get a clear understanding of potential threats.
- Security recommendations are provided – Best practices for ongoing security are included.
6. Post-Audit Support (Optional)
Security doesn’t stop when the audit ends. Our framework includes:
- Real-Time Monitoring – Keeping an eye on potential threats post-launch.
- Incident Response – Helping teams react quickly in case of security breaches.
- Insurance Options – Providing additional safety nets for unforeseen risks.
Why Does This Approach Matter?
1. Traditional Audits Aren’t Enough
Security audits often fail because they don’t go deep enough. Many projects undergo surface-level reviews that check for basic vulnerabilities but miss more complex attack vectors, the kind that real attackers exploit.
A robust security process must go beyond just looking for known issues; it should anticipate how an attacker might think, identifying hidden logic flaws, protocol interactions, and edge cases that automated scanners might overlook.
2. Automation and Manual Review Work Better Together
Automated security tools are excellent at quickly scanning for well-documented vulnerabilities like reentrancy, integer overflows, and access control misconfigurations.
However, they lack the ability to understand business logic, contract interactions, and the broader context of an application.
Manual auditors bring experience and intuition, allowing them to catch logical errors, economic exploits, and game-theoretic vulnerabilities that automation would miss.
By combining automated analysis with expert-driven manual reviews, the audit process ensures that both structural and contextual vulnerabilities are identified.
3. Independent Verification adds a Critical Layer of Assurance
Even the best auditors can overlook something.
That’s why relying solely on internal reviews can be risky. By bringing in an independent team, the Vigilant Squad, the audit process gains an external perspective that eliminates bias.
These researchers operate with fresh eyes, using their own methodologies to double-check findings, explore untested attack surfaces, and validate that all issues have been properly addressed.
This independent verification reduces the chances of any security gap slipping through before deployment.
4. Security Doesn’t End After an Audit
A security audit isn’t a one-time fix, it’s just the beginning.
The blockchain landscape is constantly evolving, with new vulnerabilities, attack techniques, and protocol interactions emerging regularly.
That’s why security should be an ongoing effort rather than a one-off event.
Post-audit support helps projects address new threats, monitor for anomalies, and adapt their security measures over time.
Whether it’s through periodic re-audits, real-time monitoring, or emergency response services, continued security vigilance ensures long-term resilience against threats.
Multi-Layered Auditing will become a Standard
At QuillAudits, we believe security isn’t just about finding vulnerabilities, it’s about building trust.
As the industry grows, projects can no longer afford to rely on one-time security stamps.
Instead, they need a continuous, layered, and transparent approach that prioritizes resilience over quick fixes.
That’s what we’re building.
That’s why we do things differently at QuillAudits.