What is Homomorphic Encryption: Explained
What is homomorphic encryption? Learn about its types, applications, and limitations in our detailed guide.

Ever wonder how you can keep your data locked up tight while still allowing it to do the heavy lifting? Homomorphic encryption might just be the magic trick you're looking for! Imagine a world where your sensitive data can be computed upon without ever needing to be decrypted. Intrigued? Let’s dive into the fascinating realm of homomorphic encryption and uncover its secrets.
What is Homomorphic Encryption?
Homomorphic encryption is a technique that transforms data into ciphertext, allowing it to be analyzed and worked with as though it were still in its original, unencrypted state. This encryption method facilitates performing complex mathematical operations on the encrypted data without ever exposing or compromising the original information.
At its core, homomorphic encryption is like having a secret code that not only protects your data but allows you to perform calculations on it while it’s still in its encrypted form. Imagine being able to work with sensitive information without ever having to expose it—like sending a package that can be weighed, measured, and even manipulated without ever opening it.
This is the magic of homomorphic encryption: it creates a secure environment where data can be used to its fullest potential without compromising its confidentiality. Think of it as a high-tech privacy shield that lets your data do its job without revealing its true self.
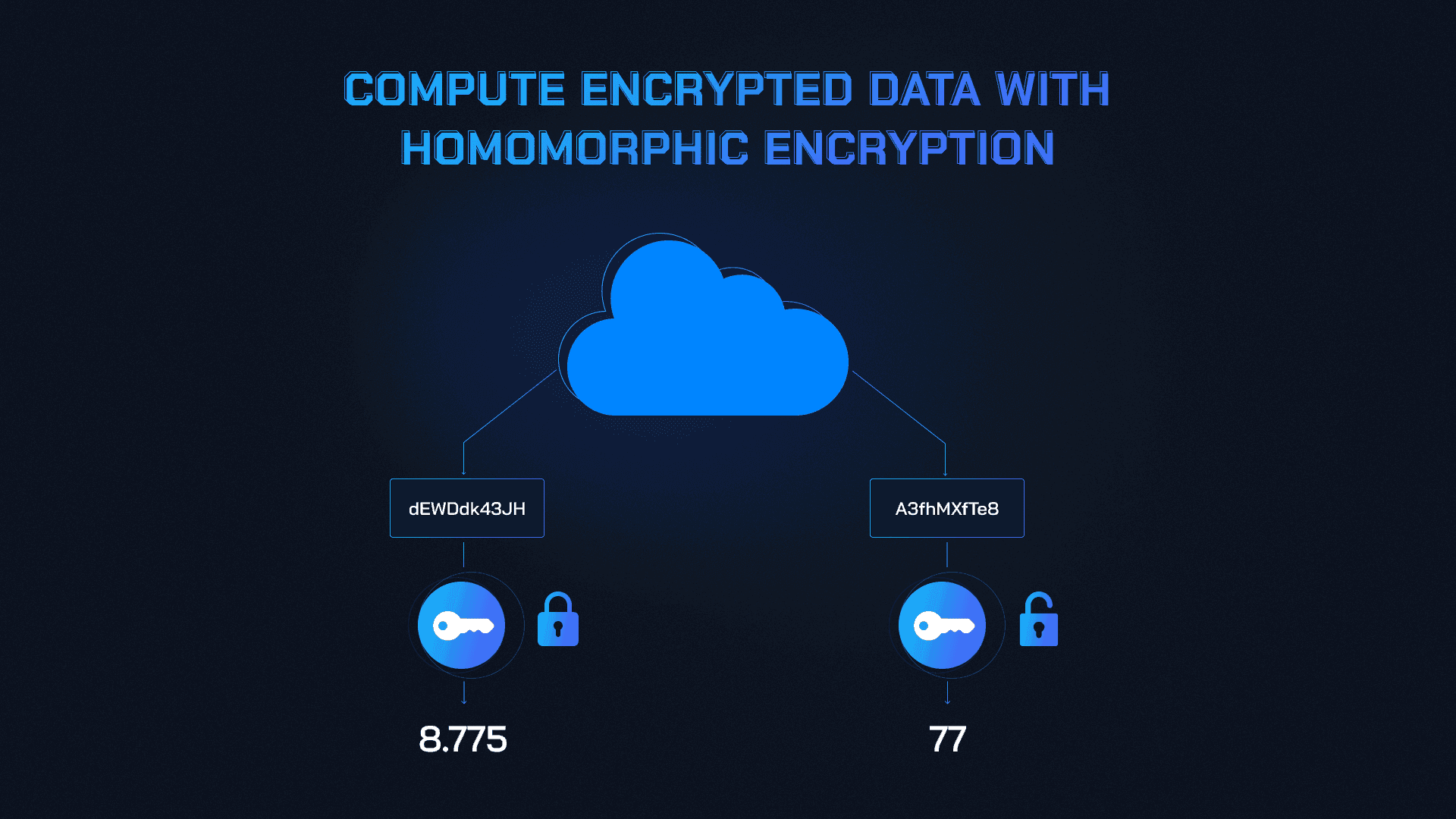
In traditional encryption, you lock up your data with a public key, ensuring that only the holder of the corresponding private key can access the original, unencrypted information. This is great for keeping data safe from prying eyes, but it becomes a challenge when you need to perform computations on that data. Normally, you’d have to decrypt it first, exposing it to potential risks.
Homomorphic encryption, however, takes this a step further by allowing computations to be performed directly on the encrypted data itself. This means you can carry out operations like addition, multiplication, and more without ever needing to see the data in plaintext. The result? An encrypted output that can only be understood by someone with the private key, ensuring that your data remains secure throughout the entire process.
Holomorphic encryption, on the other hand, is a term that is sometimes confused with homomorphic encryption due to the similarity in spelling. However, holomorphic encryption is not a recognized cryptographic term. The correct concept is homomorphic encryption, which revolutionizes how data can be securely processed and analyzed in environments where privacy and security are paramount.
What’s in a Name? The Mystery of ‘Homomorphic’
The term "homomorphic" comes from Greek roots, with "homo" meaning "same" and "morphic" meaning "structure." In the world of mathematics, this concept refers to a transformation that maintains the underlying relationships between elements, even as they change form. It's akin to reshuffling a deck of cards without altering the order of the suits and numbers—everything still relates in the same way, even if the appearance has changed.
When we apply this idea to encryption, homomorphic encryption ensures that operations performed on encrypted data yield results consistent with those you’d get if you were working with the plaintext data. Imagine you’re using a secret code to write a message. With homomorphic encryption, you can add or subtract numbers, multiply, and even execute complex operations on the coded message, and the outcome will still align perfectly with what you’d expect if you were doing the same operations on the original, unencrypted message.
It’s like being able to understand the essence of a book while only seeing the encrypted text—you can still determine the plot, analyze character development, and draw conclusions, all without ever cracking the code. This consistency is the magic of homomorphic encryption: it preserves the integrity and relationships of data, allowing it to be used in a meaningful way even when hidden behind layers of encryption.
So, why does this matter? In practical terms, homomorphic encryption allows data to be processed in secure environments—like cloud servers—without ever exposing the sensitive information to potential threats. Whether you’re analyzing financial transactions, processing healthcare records, or running predictive models, homomorphic encryption ensures that your data remains both useful and secure.
Types of homomorphic encryption
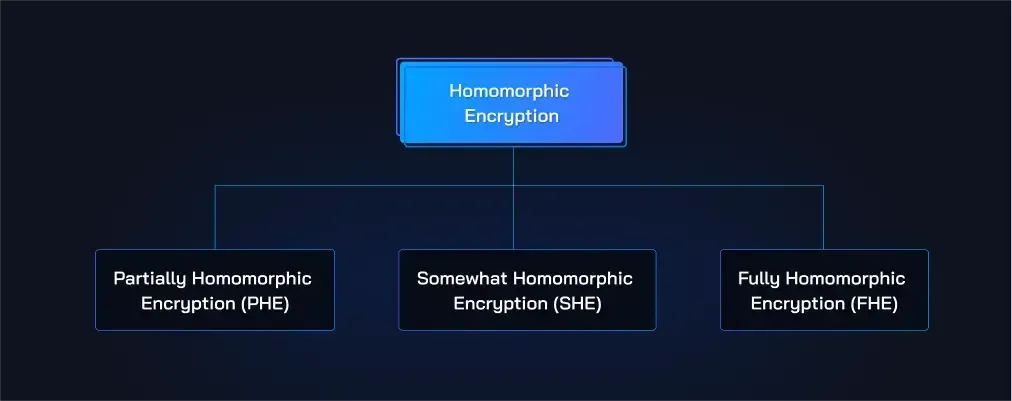
Homomorphic encryption isn’t a one-size-fits-all solution; it comes in different flavors, each tailored to specific needs and with varying degrees of complexity and capability. Just like the legendary Three Musketeers, these three categories of homomorphic encryption—
- Partially Homomorphic Encryption (PHE),
- Somewhat Homomorphic Encryption (SHE), and
- Fully Homomorphic Encryption (FHE)
each bring their unique strengths to the table, working together to protect and process data securely. Let's dive into what makes each of these "musketeers" special.
- Partially Homomorphic Encryption (PHE) PHE is the first of the trio and could be considered the specialist of the group. This encryption method allows for specific types of mathematical operations—either addition or multiplication—on encrypted data, but not both. Imagine you’re a chef with the ability to prepare either only appetizers or only desserts, but never a full meal. That’s PHE in a nutshell. It’s particularly useful in scenarios where you only need to perform one type of operation repeatedly. For instance, RSA encryption, widely used in secure communications like SSL/TLS protocols, is an example of multiplicative PHE. With RSA, you can multiply encrypted numbers as much as you like, but the moment you need to add them, you’re out of luck. This makes PHE perfect for certain applications, but limited when you need more versatility.
- Somewhat Homomorphic Encryption (SHE) Stepping up the game is Somewhat Homomorphic Encryption (SHE), the all-rounder who can handle a bit more complexity. SHE supports a limited number of operations, either addition or multiplication, but with a catch—you can only perform these operations up to a certain level of complexity before the system starts to bog down. Think of SHE as a calculator that’s great for basic math problems, but starts to struggle with more advanced equations. SHE is a bridge between PHE and FHE, offering more flexibility than PHE while not requiring the heavy computational resources of FHE. It’s like a jack-of-all-trades, capable of juggling multiple tasks, but with limitations that prevent it from handling the most demanding jobs.
- Fully Homomorphic Encryption (FHE) Finally, we have Fully Homomorphic Encryption (FHE), the grandmaster of homomorphic encryption. FHE is the all-powerful super-calculator of the group, capable of handling unlimited addition and multiplication operations on encrypted data. Imagine a superhero who can perform any feat, no matter how complex, while remaining completely invisible. That’s FHE. It’s the dream of cryptographers, allowing for any computation to be carried out on encrypted data without ever needing to decrypt it. This makes FHE incredibly powerful for applications like secure multi-party computation, where different parties can collaborate on encrypted data without revealing their individual inputs. The promise of FHE lies in its ability to harmonize privacy and functionality, enabling sophisticated data analysis and processing in untrusted environments, like the cloud, without ever exposing the underlying data.
However, with great power comes great responsibility—and in FHE’s case, significant computational overhead. While it’s the most versatile of the three, FHE requires substantial computational resources, making it slower and more resource-intensive compared to PHE and SHE. Despite these challenges, FHE is seen as the future of secure data processing, with ongoing research aimed at making it more efficient and accessible for real-world applications.
Apply for the WAGSI Grants Now!
Apply for the WAGSI Grants Now!
Take advantage of the WAGSI Grants to finance your project and implement your innovative ideas.
Applications of homomorphic encryption
You might be asking, "Why go through the trouble of homomorphic encryption?" It’s a valid question after all, traditional encryption methods have served us well for years. However, homomorphic encryption isn’t just another tool in the cryptographic toolbox; it’s a game-changer that addresses specific, critical challenges in modern data security. Let’s explore why homomorphic encryption is worth the effort:
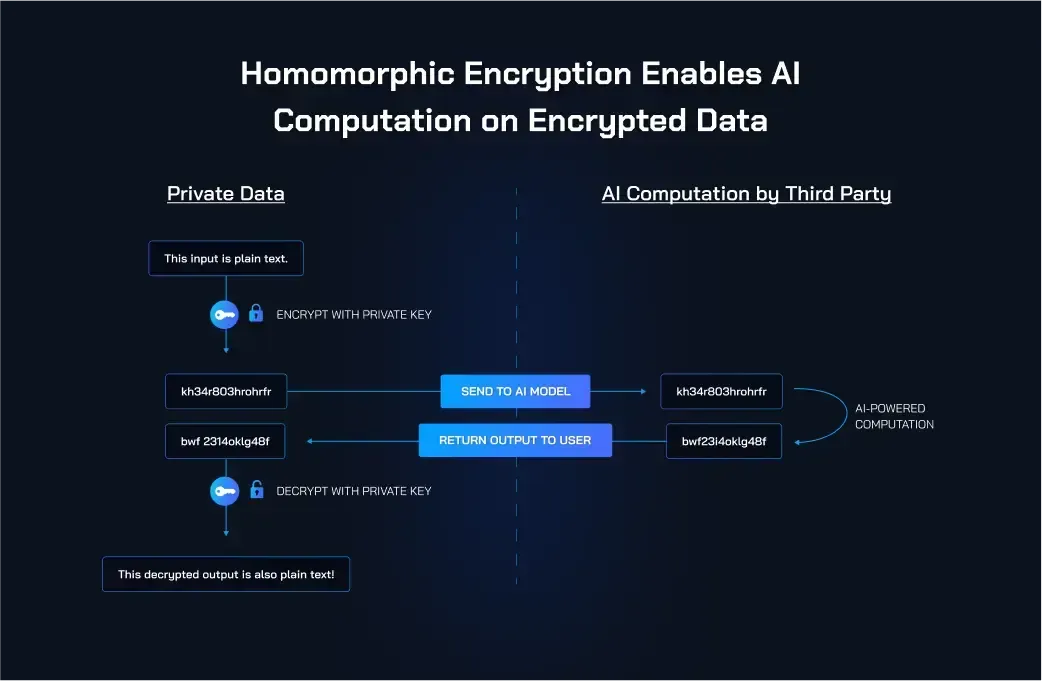
- Privacy in the Cloud: The Ultimate Security Upgrade The cloud has revolutionized how we store and process data, offering scalability and convenience that was once unimaginable. However, this convenience comes with a significant trade-off—privacy. Typically, when data is stored in the cloud, it must be decrypted before any processing can occur. This decryption process exposes the data to potential breaches, whether through unauthorized access, malicious insiders, or vulnerabilities in the cloud infrastructure. Homomorphic encryption flips this script by allowing computations to be performed directly on encrypted data. This means your sensitive information never has to be decrypted, drastically reducing the risk of exposure. Imagine being able to run complex algorithms, machine learning models, or even simple database queries on your encrypted data in the cloud without ever worrying that your private information might leak. That’s the power of homomorphic encryption—keeping your secrets safe, even in environments that you don’t fully control.
- Secure Data Analysis: Privacy Without Compromise
In today’s data-driven world, organizations need to analyze vast amounts of information to gain insights, make decisions, and drive innovation. However, this often involves working with sensitive data that must be protected, especially in regulated industries like healthcare, finance, and government. Homomorphic encryption allows organizations to perform data analysis on encrypted datasets without exposing the underlying data. For example, in the healthcare sector, homomorphic encryption could enable researchers to analyze patient records from multiple hospitals to find trends and correlations, all without ever accessing the actual patient information. Similarly, financial institutions could run risk assessments on encrypted financial data to detect fraud or evaluate loan applications while ensuring that individual privacy is never compromised. By enabling secure data analysis, homomorphic encryption empowers organizations to unlock the full potential of their data while upholding the highest standards of privacy and compliance.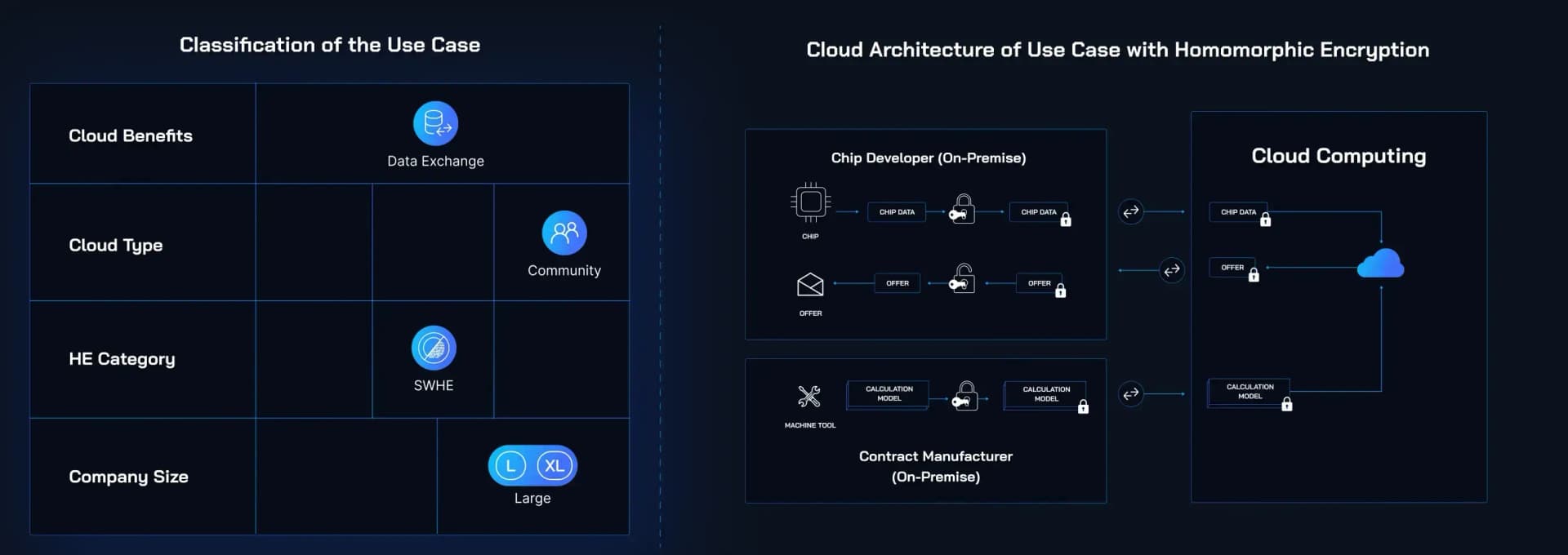
- Enhanced Security for Voting Systems: Protecting Democracy Voting systems are the cornerstone of democratic societies, and their integrity is paramount. However, ensuring both the accuracy and privacy of votes is a complex challenge. Traditional electronic voting systems often require a trade-off between transparency and confidentiality—voters need assurance that their votes are counted correctly, but their choices must also remain private. Homomorphic encryption offers a solution that could transform how we conduct elections. By encrypting votes, homomorphic encryption allows for secure, transparent tallying without revealing individual voter preferences. The election authority can sum the encrypted votes, and only after the tallying is complete can the final result be decrypted, ensuring that the process remains both secure and verifiable. This technology could pave the way for more secure and trustworthy voting systems, reducing the risk of tampering, fraud, and voter coercion. Imagine a future where citizens can vote electronically, knowing that their vote is both private and secure, and the results are beyond reproach—that’s the promise of homomorphic encryption in the electoral process.
Limitations of Homomorphic Encryption
If homomorphic encryption is so powerful, why isn’t it the standard for data security everywhere? The answer lies in a combination of factors that make HE, especially FHE, difficult to implement on a large scale. Here’s why HE hasn't yet become ubiquitous:
- Computational Cost: The Price of Privacy Homomorphic encryption is computationally intensive. The amount of processing power required to perform even basic operations on encrypted data is significantly higher than with traditional encryption methods. This high computational cost has been a significant barrier to widespread adoption, particularly for applications that require real-time processing or have limited resources. The cost of deploying HE can also be a deterrent, as it often requires expensive hardware and extensive computational resources, making it less accessible for smaller organizations or those with tight budgets.
- Noise Accumulation: The Technical Hurdle One of the technical challenges with HE is noise accumulation during computations. Each operation on encrypted data introduces a small amount of noise, and over time, this noise can build up, potentially corrupting the results and rendering the data unusable. This phenomenon is particularly problematic in FHE, where complex and repeated operations can lead to significant noise accumulation. While techniques like bootstrapping can clean up this noise, they add additional computational overhead, further slowing down the process. Managing this noise effectively is one of the key challenges in making HE practical for everyday use.
- Complexity: The Steep Learning Curve
Implementing and maintaining homomorphic encryption systems is far from straightforward. The mathematics behind HE is highly complex, requiring specialized knowledge to implement effectively. This complexity increases the risk of errors in the implementation, making it more challenging to develop robust and secure HE solutions. The steep learning curve also means that there are fewer experts capable of working with HE, limiting its adoption in industries where security is paramount but expertise in advanced cryptography may be lacking.
- Limited Practical Implementations: The Gap Between Theory and Practice
Although FHE theoretically supports any computation on encrypted data, practical implementations have been limited. Many current applications of HE are confined to simpler operations or require substantial simplifications to be feasible. This limitation means that many potential use cases for HE, such as large-scale data analytics or real-time processing, are still beyond the reach of current technology. The gap between the theoretical potential of HE and its practical applications is one of the main reasons why it hasn’t yet become a standard tool in data security.
Remedies and Ongoing Research
Despite these challenges, the field of homomorphic encryption is rapidly advancing, with researchers and innovators working on several promising solutions to make HE more practical and scalable:
- Trusted Execution Environments (TEEs): Combining Security Layers Trusted Execution Environments (TEEs) provide a secure area within a processor where computations can be performed safely, even in potentially compromised environments. By combining HE with TEEs, it’s possible to offload some of the computational burden while maintaining strong security guarantees. TEEs can help mitigate some of the performance issues associated with HE by providing a secure environment for critical operations, thereby reducing the need for full encryption while still protecting sensitive data.
- Improved Algorithms: Paving the Way for Efficiency Advances in HE algorithms, such as more efficient noise management techniques and optimized encryption schemes, are helping to reduce the computational overhead associated with HE. These improvements are making HE more practical for a broader range of applications, from secure cloud computing to privacy-preserving data analytics. For instance, newer schemes like TFHE and CKKS are being developed to balance noise tolerance with computational efficiency, making them more suitable for real-world use.
- Hardware Acceleration: Speeding Up the Process Specialized hardware, such as FHE-specific coprocessors or GPUs, can significantly accelerate HE operations. Companies like Optalysys and Cysic are developing hardware solutions designed to speed up HE computations, making them more feasible for real-world applications. By leveraging hardware acceleration, it’s possible to mitigate some of the performance drawbacks of HE, bringing it closer to parity with traditional encryption methods in terms of speed.
- Noise Reduction Techniques: Keeping the Data Clean Researchers are exploring new methods to manage and reduce noise accumulation in HE systems. Techniques like bootstrapping have been refined to be more efficient, and newer approaches like the BGV and BFV schemes offer improved noise management. These advancements are critical in making HE more reliable and scalable, as they directly address one of the most significant technical challenges in the field.
- Layered HE Architectures: Tailoring Solutions to Needs By using a combination of different HE types, such as Partially Homomorphic Encryption (PHE), Somewhat Homomorphic Encryption (SHE), and Fully Homomorphic Encryption (FHE), it’s possible to create layered encryption schemes that optimize performance for specific use cases. For instance, PHE or SHE might be used for less sensitive operations where speed is essential, while FHE is reserved for critical computations that require the highest level of security. This layered approach allows for more flexible and practical implementations of HE, tailored to the specific needs of different applications.
If Homomorphic encryption interests you, you will absolutely love this playlist of FHE Summit 2024 by FHEOnChain.
Wrapping It Up

Check Out Our Work
We've audited top DApps and DeFi protocols, ensuring they remain secure and Free from Hacks. Check out their audit reports to see our impact.

Homomorphic encryption is like a cloak of invisibility for your data. It lets you perform computations without ever needing to reveal the actual information, making it a game-changer for privacy and security. While it’s still evolving, the potential applications—from secure cloud computing to privacy-preserving data analytics—are vast and exciting.
So, next time you think about securing your data, remember that with homomorphic encryption, you don’t have to choose between privacy and functionality. You can have both!
At QuillAudits, we continuously explore emerging cryptographic advancements like homomorphic encryption to stay ahead in securing decentralized ecosystems. While this technology is still evolving, its potential to enable secure, privacy-preserving computations aligns with our mission to deliver next-gen Web3 security solutions for smart contracts, dApps and DeFi protocols.
Contents