Decoding UwU Lend’s $19.4 Million Exploit
Discover how UwU Lend's $19.4M exploit happened, its Vulnerability Analysis & Impact. Read our analysis of the hack and its far-reaching consequences.

Summary
On the 10th of June, 2024, Uwu Lend was attacked resulting in a loss of more than $19.4 million.
About Project
UwU Lend is a decentralized non-custodial liquidity market protocol where users can participate as depositors, borrowers or LP stakers. To learn more about UwU Lend, head over to https://uwulend.fi/
Vulnerability Analysis & Impact
On-Chain Details
Attacker Address: 0x841ddf093f5188989fa1524e7b893de64b421f47
Attacker Contract: 0x21C58d8F816578b1193AEf4683E8c64405A4312E
Attacker Transactions: https://etherscan.io/address/0x841dDf093f5188989fA1524e7B893de64B421f47
The Root Cause
The USDe oracle on UwU Lend uses the median of 11 price sources. However, 5 of these sources were easily manipulated using CurveFinance pools.
The transactions by the attacker can be seen below.
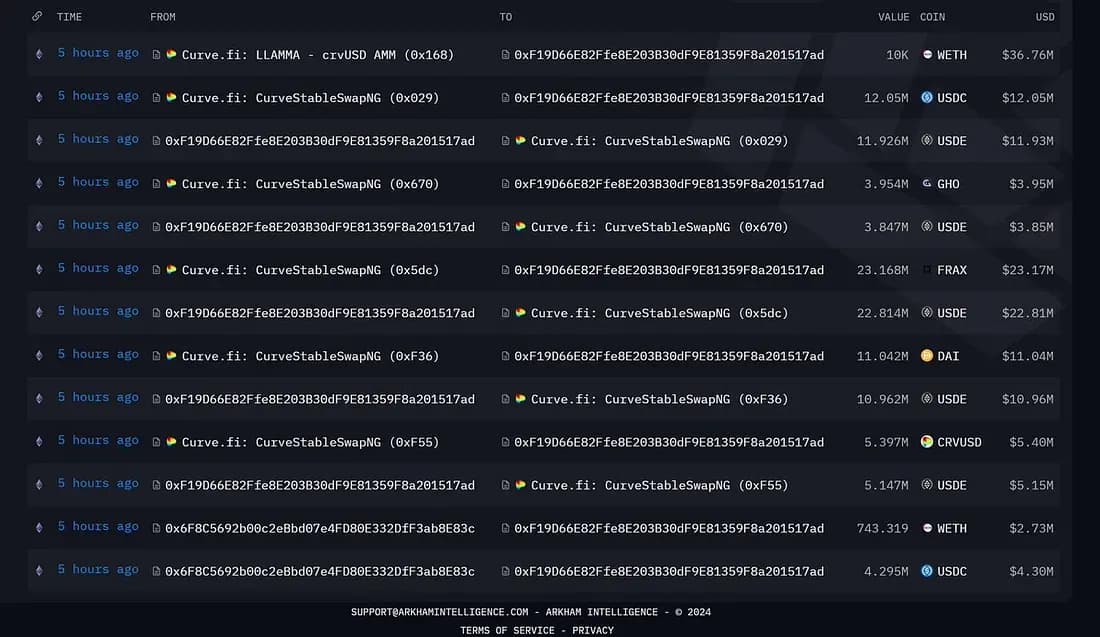
Attack Process
The price of sUSDe on the Curve Finance oracle was manipulated down by 4% to enable borrowing at $0.99. When the price went back up to $1.03, liquidations occurred, leading to substantial gains for the attacker. UwU and its lenders faced losses because of aggressive rehypothecation through repeated borrowing and lending.
Rehypothecation is a practice whereby banks and brokers use, for their own purposes, assets that have been posted as collateral by their clients.
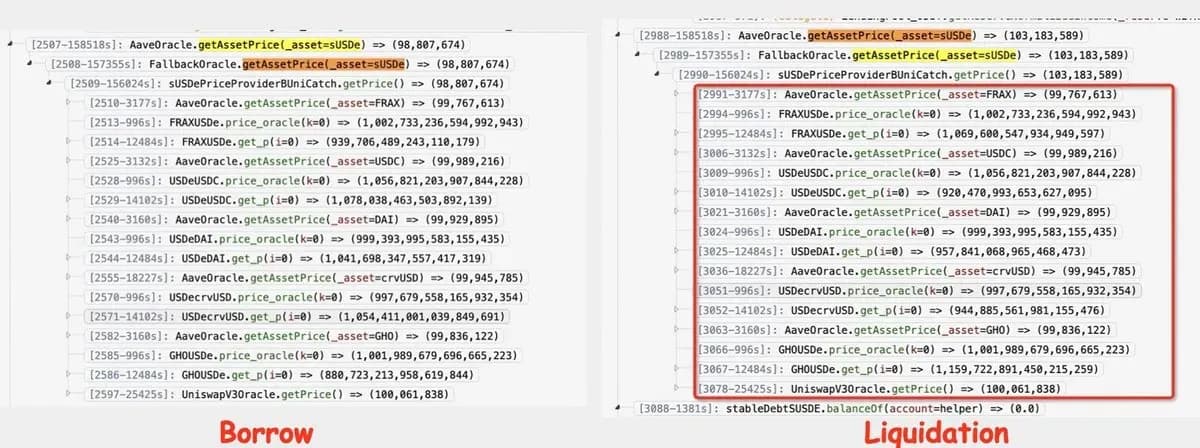
The UwU Lend oracle uses the get_p function to fetch the instantaneous spot price without any smoothing, despite Curve Finance advising against this practice. This oversight lowered the cost of the attack. With $173 million in these pools, the attacker used a 40K ETH flash loan to exploit the system.
Flow of Funds
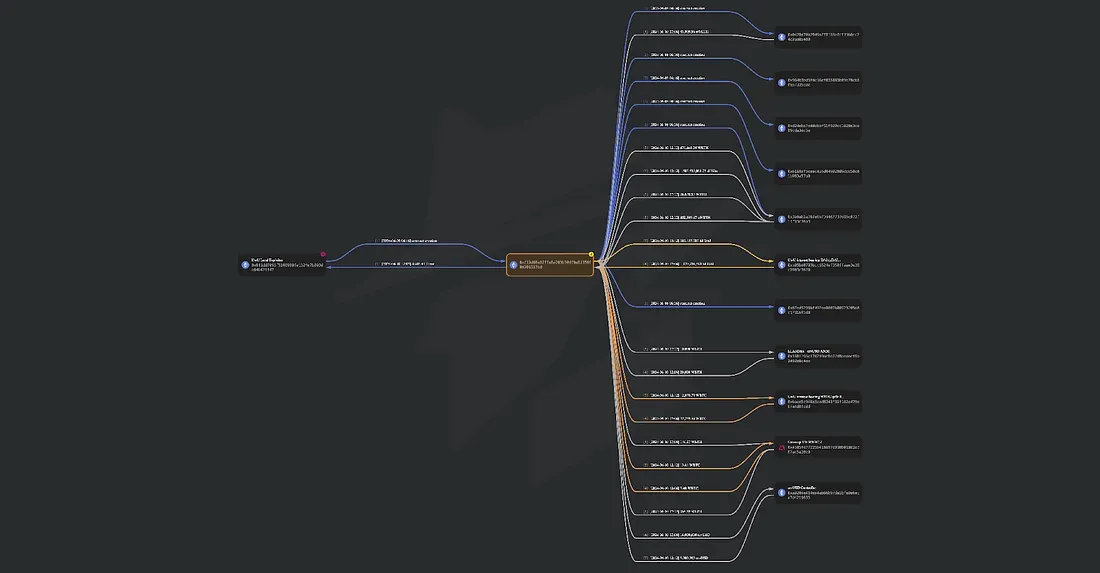
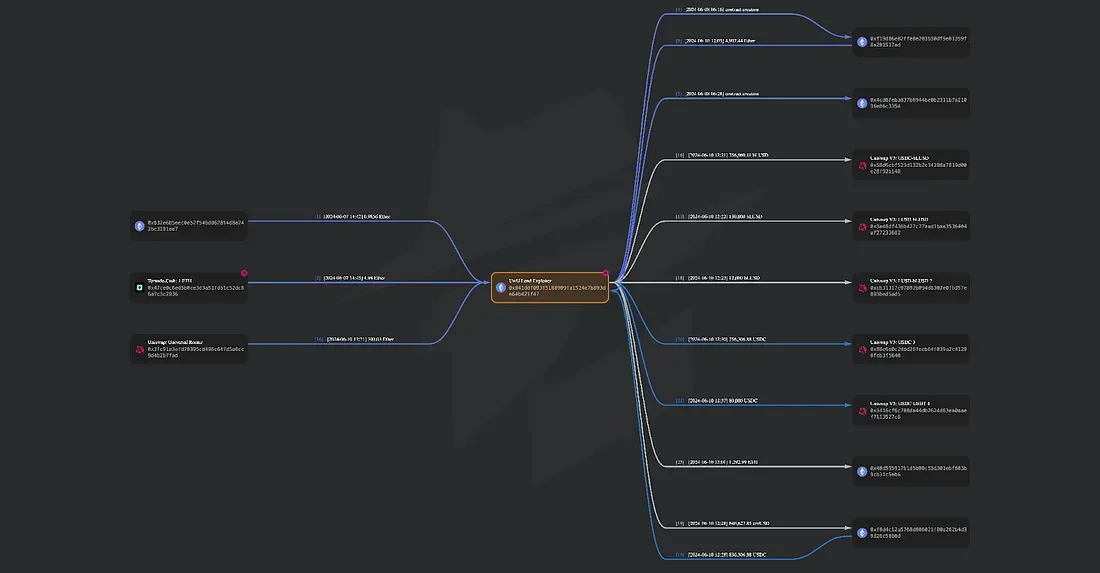
After the Exploit
The hack was first noticed by Cyvers, an on-chain security firm, which alerted UwU Lend when the stolen amount was $14 million. The amount quickly surpassed $20 million.
The protocol was paused soon after the exploit and UwU Lend acknowledged the exploit through their official X handle.
How could they have prevented the exploit?
The exploit could have been avoided by developing robust oracle prices based on a thorough understanding of liquidity dynamics. While using a median of 11 price feeds might appear secure, low liquidity in half of these feeds and the absence of price smoothing made it easy for the attacker to gain an advantage.
With five weak feeds, manipulating just one strong feed could shift the median. Relying solely on strong feeds would have increased the cost of manipulation. Implementing carefully designed smoothing and weighting mechanisms is crucial to raising the cost of manipulation while ensuring the price oracle remains accurate and resilient against attacks.
A full-fledged comprehensive audit of all the contracts in the protocol should be carried out by experts before launch.
Why QuillAudits For Web3 Security?
- QuillAudits is well-equipped with tools and expertise to provide cybersecurity solutions saving the loss of hundreds of protocols in funds.
- Our team of highly skilled auditors have secured over 1M lines of code and $3B in amount.
- Over the course of multiple years, QuillAudits has been proven to be one of the top choices for protocols to get their codebases audited.
Partner with QuillAudits
- OG Program (Opportunities for Listing Managers, KOLs, Top Advisors and Investors with access to early stage Web3 projects)
- QuillAudits Partnership Programme (Venture funds, launchpads, development companies, marketing firms, web2 cybersecurity firms, web3 products)
- WAGSI Program(Claim audit credits to avail exclusive discounts on our auditing package, and additional credits for our automated web3 security infra- QuillShield)
Contents


