Decoding Shezmu’s $4.9 Million Exploit
Read our in-depth hack analysis on Shezmu's $4.9 Million Exploit, uncovering vulnerabilities, attack details, and security insights

Overview
On September 20, 2024, Shezmu suffered a $4.9 million exploit due to a vault vulnerability that allowed unauthorized collateral minting. The hacker used this flaw to drain the protocol but agreed to return the stolen funds in exchange for a 20% bounty after negotiations. Shezmu's recent contract upgrade on September 3 may have introduced or left the vulnerability unaddressed.
About Project
Shezmu token is a cutting-edge digital asset designed to empower the decentralized finance (DeFi) ecosystem by providing a seamless and secure means of transaction processing. Built on the Ethereum blockchain, this innovative token leverages the power of smart contracts to facilitate fast, low-cost, and transparent transactions. At the heart of Shezmu's architecture lies its proprietary consensus algorithm, which ensures the integrity and security of the network.
Exploit Details
Attack Contract address: 0xEd4B3d468DEd53a322A8B8280B6f35aAE8bC499C
Shezmu Attacker address (created attack contract): 0xA3a64255484aD65158AF0F9d96B5577F79901a1D
Attack Contract Creation tx: 0x39328ea4377a8887d3f6ce91b2f4c6b19a851e2fc5163e2f83bbc2fc136d0c71
Secure Your Smart Contracts with QuillAudits
Secure Your Smart Contracts with QuillAudits
Ready to secure your smart contracts? Take the first step towards a safer blockchain journey. Request an Audit with QuillAudits today & ensure your contracts are robust and secure!
Attack Process
- The hacker identified a critical flaw in Shezmu’s vault, allowing anyone to mint collateral freely.
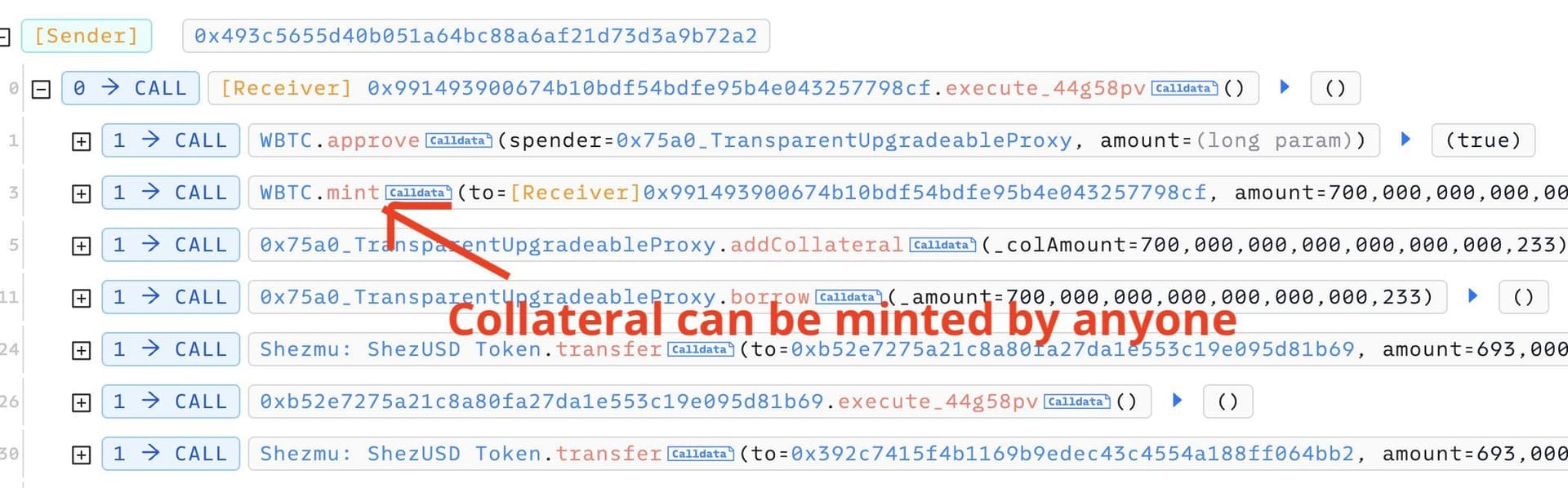
- The attacker developed a custom smart contract designed to exploit this vulnerability.
- Using the custom contract, the hacker minted a large amount of ShezUSD without the required collateral.
With the minted ShezUSD, the hacker borrowed a significant portion of the protocol's resources, effectively draining $4.9 million.
The Root Cause
The root cause of the Shezmu exploit was a critical vulnerability in their vault system that allowed unauthorized minting of collateral. This flaw enabled the attacker to mint ShezUSD freely, bypassing the necessary checks or collateral requirements.
The vulnerability likely stemmed from a contract upgrade implemented on September 3, which may have introduced the bug or failed to address an existing issue.
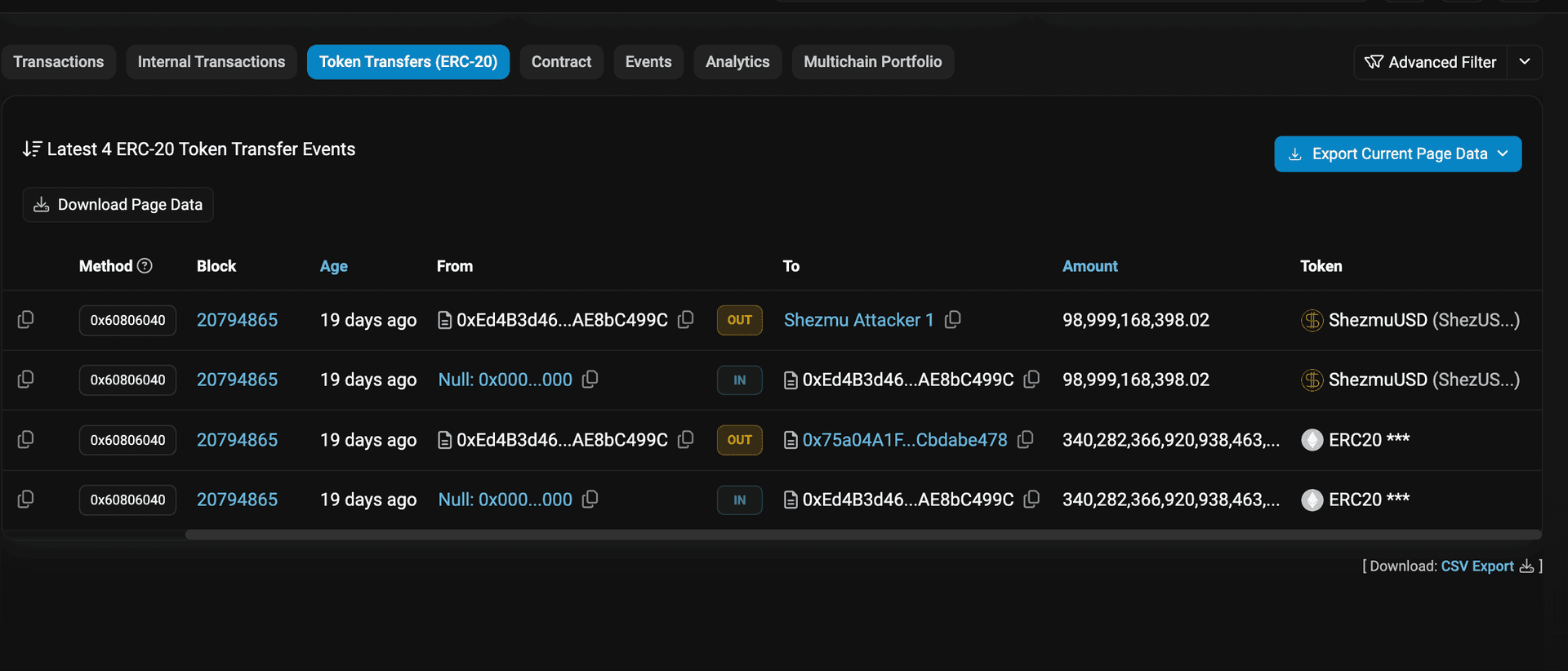
Flow of Funds
The attacker minted ShezUSD using the vulnerability and borrowed funds from the protocol, draining $4.9 million worth of assets. Here is the fund flow.
Post Exploit Scenes
Here is what Shezmu responded to the exploit:
One of the ShezUSD vaults has been compromised. Please avoid using the dApp for now. We're investigating the cause of the exploit and will offer a bounty while reaching out to the appropriate authorities. A detailed post-mortem will follow soon.
The attacker returned the stolen funds to Shezmu after both parties agreed on a 20% bounty.
How could they have prevented the Exploit?
- Engage reputable audit firms like QuillAudits to conduct comprehensive security audits, especially after contract upgrades, to identify vulnerabilities such as unauthorized collateral minting.
- Implement strict access control mechanisms to ensure only authorized users can mint or manage collateral.
Apply for the WAGSI Grants Now!
Apply for the WAGSI Grants Now!
Take advantage of the WAGSI Grants to finance your project and implement your innovative ideas.
Why QuillAudits?
Choosing a reputable audit firm like QuillAudits ensures that your protocol undergoes rigorous scrutiny from experienced security professionals. QuillAudits specializes in uncovering critical vulnerabilities and providing actionable remediation strategies. Our expertise helps safeguard your project from attacks, ensuring that security issues are addressed proactively.
Contents




