Decoding Penpie Protocol’s $27M Exploit
Discover how Penpie Protocol faced a $27M exploit. What went wrong? Uncover the shocking details with QuillAudits behind this massive breach!

Overview
Yesterday, Penpie, a farming protocol built on the Pendle Protocol, recently fell victim to a devastating reentrancy attack that resulted in a massive loss of approximately $27 million. The attack exploited vulnerabilities in the PendleStaking contract, which lacked crucial security measures such as reentrancy guards. This failure allowed the attacker to manipulate markets, harvest rewards maliciously, and withdraw significant amounts of value.
The exploit underscores the critical need for robust security practices in decentralized finance (DeFi) protocols.
TLDR: What Went Down?
Penpie’s $27M exploit was triggered by a reentrancy vulnerability within its PendleStaking implementation. An attacker leveraged a counterfeit SY token and manipulated high-value PENDLE-LPT tokens to exploit the system. The attack involved a series of strategic moves, including flash loans and token manipulation, to siphon off substantial amounts of valuable tokens. The lack of reentrancy guards and proper market validation made this exploit possible.
The Attack in Action: From Zero to $27M
- Getting the Ball Rolling
- Fake It ‘Til You Make It: The attack began with the creation of a counterfeit SY (standardized yield) token, specifically
0x4476b. Despite these tokens being worthless, they set up the attacker for further exploitation.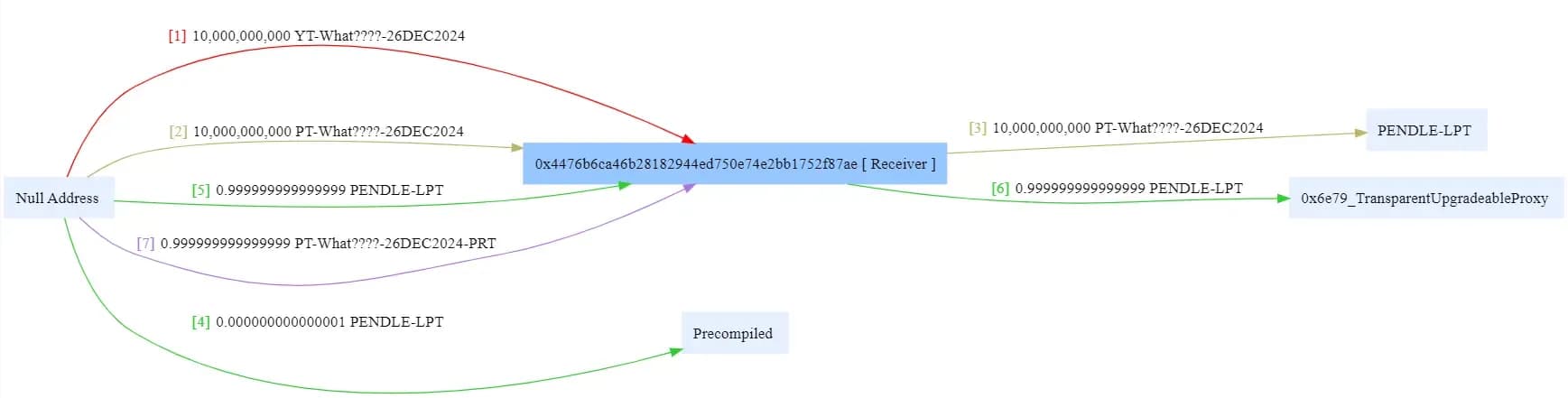
Market Magic: Armed with high-value PENDLE-LPT tokens (
0x6010_PENDLE-LPTand0x038c_PENDLE-LPT), the attacker created a new market on Penpie. This market, despite being fraudulent, was accepted and recognized by the protocol due to inadequate validation.
Attack Prep Transaction: https://app.blocksec.com/explorer/tx/eth/0x7e7f9548f301d3dd863eac94e6190cb742ab6aa9d7730549ff743bf84cbd21d1
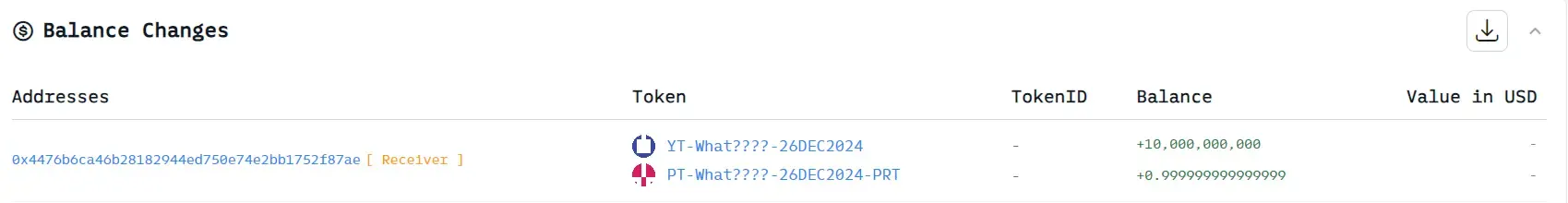
- Fake It ‘Til You Make It: The attack began with the creation of a counterfeit SY (standardized yield) token, specifically
- Making It Rain
- Harvest Time: The attacker executed the
batchHarvestMarketRewards()function, which calculated rewards based on the token balances before and after callingredeemRewards().
- Reentrancy Shenanigans: By triggering the
redeemRewards()function, which calledclaimRewards()of the specific market, the attacker exploited the contract’s reentrancy vulnerability. The lack of proper validation allowed them to re-enter the contract via thedepositMarket()function repeatedly.
- Token Deposits Galore: The attacker deposited high-value LPT market tokens, which were mistakenly treated as rewards by Penpie. This led to the minting of shares in their favor and allowed them to withdraw valuable LPT tokens and minted shares, realizing a significant profit.
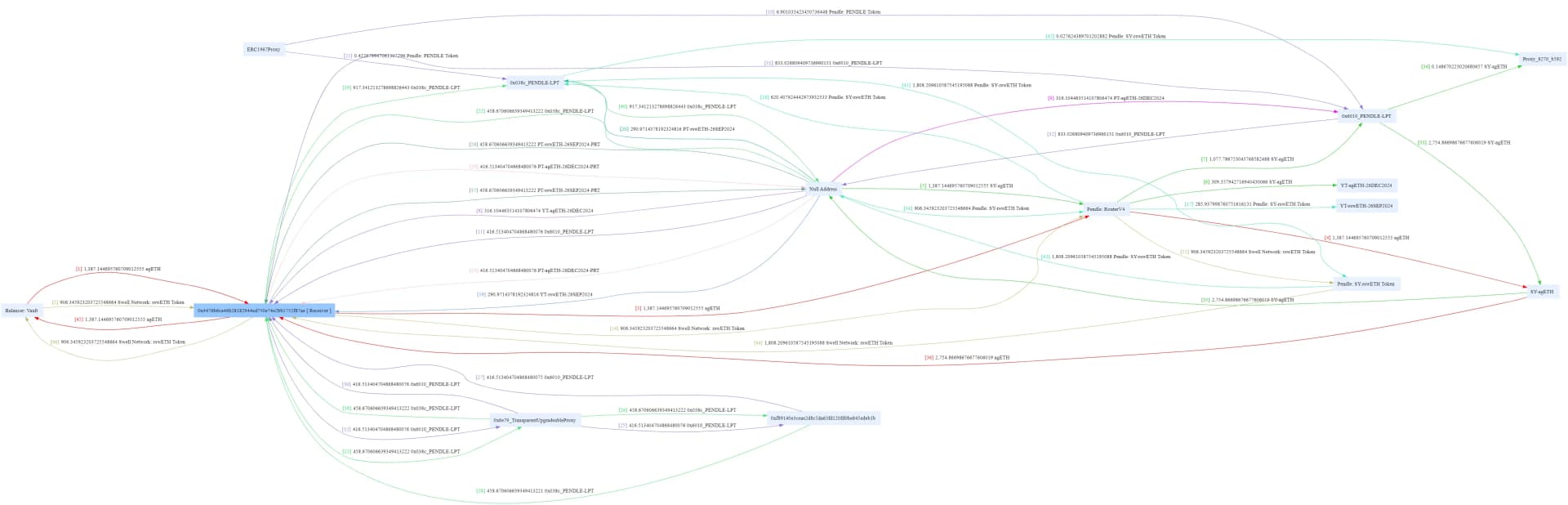
Attack Transaction:
https://app.blocksec.com/explorer/tx/eth/0x42b2ec27c732100dd9037c76da415e10329ea41598de453bb0c0c9ea7ce0d8e5
- Harvest Time: The attacker executed the
- Flash Loans and Token Twisting
- Loan Sharks: Flash loans from the Balancer pool, specifically $agETH and $rswETH, were used to facilitate the attack. These loans provided the necessary liquidity for the exploit to begin with.
- Token Tinkering: The attacker minted large quantities of malicious YT/PT tokens and transferred them within Pendle. These tokens were then deposited into Penpie, impacting tokens like $wstETH, $sUSDe, and $rswETH.
- Loan Sharks: Flash loans from the Balancer pool, specifically $agETH and $rswETH, were used to facilitate the attack. These loans provided the necessary liquidity for the exploit to begin with.
- Post-Exploit Shuffle
- Hiding the Loot: To obscure their tracks, the attacker moved ~3.3K $ETH (worth ~$7.92M) through Tornado Cash for laundering. Approximately 10.11K stolen $ETH (worth ~$24.7M) was left at address
0x2f2d...1C39.
- Hiding the Loot: To obscure their tracks, the attacker moved ~3.3K $ETH (worth ~$7.92M) through Tornado Cash for laundering. Approximately 10.11K stolen $ETH (worth ~$24.7M) was left at address
Key Details
Attacker address:
0x7a2f4d625fb21f5e51562ce8dc2e722e12a61d1b (ethereum and arbitrum)
Exploit contract:
0xcde2cd6aeaaf0238f4ce33295be13704e4a97de2 (ethereum)
0x4bc9815b859c8172cee1ab2cd372fd0eb00eb487 (arbitrum)
PendleStaking contract: 0xFF51c6b493c1E4Df4e491865352353EAdff0f9f8 (ethereum)
Attack transactions:
0x67c5400da117b906f8c0fc5f5149e4ea10ed6358cd9ea2ec0ed8f559d757b7df (arbitrum)
0x56e09abb35ff12271fdb38ff8a23e4d4a7396844426a94c4d3af2e8b7a0a2813 (ethereum)
0x42b2ec27c732100dd9037c76da415e10329ea41598de453bb0c0c9ea7ce0d8e5 (ethereum)
0x663b55a1ee992603f7636ef23ff5cf19d3b261ab81494d06e218c86482df5342 (ethereum)
Root Cause: A Case of the Missing Reentrancy Guard
The Penpie exploit can be traced back to the absence of a reentrancy guard in the PendleStaking contract. This crucial security feature was missing, leaving the contract vulnerable to malicious reentrant calls. The protocol’s failure to validate the trustworthiness of the markets argument exacerbated the issue, allowing attackers to exploit the system through market manipulation. By creating a malicious market, attackers were able to inflate staking balances and claim rewards unjustly.
Post-Hack Actions: Cleaning Up the Mess
- Immediate Lockdown: Penpie took swift action by pausing the protocol to prevent further damage and to investigate the breach.
- Negotiations in the Works: Penpie is willing to negotiate a bounty for the safe return of the funds and offer the exploiter an opportunity to transition into a white-hat role.
- Community Communication: Penpie has been transparent with its community, providing updates on the breach and outlining the steps being taken to reinforce the protocol’s defenses.
Final Thoughts
The $27M exploit of the Penpie protocol underscores a crucial lesson in the importance of robust security practices in decentralized finance (DeFi). Reentrancy attacks, like the one that exploited Penpie, highlight how vulnerabilities in smart contracts can lead to catastrophic financial losses if not properly mitigated.
Reentrancy Attacks and Prevention
Reentrancy attacks occur when a contract’s external call allows a malicious actor to re-enter the contract in an unintended state, often leading to unauthorized actions or fund transfers. To prevent such attacks, here are several key strategies:
- Implement Reentrancy Guards: Incorporate reentrancy guards in contracts to prevent multiple calls from exploiting the contract state. This safeguard ensures that reentrant calls are blocked while a function is executing, thereby mitigating the risk of malicious exploitation.
- Validate External Inputs: Always validate the trustworthiness of external inputs and interactions. Ensure that contracts do not rely on untrusted data or allow arbitrary external calls that can be manipulated.
- Follow Best Practices: Adhere to best practices for secure smart contract development, including thorough testing, code reviews, and adherence to established security patterns.
- Regular Security Audits: Engage reputable security firms to conduct comprehensive audits of your smart contracts. Firms like QuillAudits offer expert insights and thorough assessments to identify and address potential vulnerabilities before they can be exploited.
Why QuillAudits?
Choosing a reputable audit firm like QuillAudits ensures that your protocol undergoes rigorous scrutiny from experienced security professionals. QuillAudits specializes in uncovering critical vulnerabilities and providing actionable remediation strategies. Their expertise helps safeguard your project from attacks, ensuring that security issues are addressed proactively.
Join 1400+ leaders who secured themselves from losing Billion Dollars.
In the world of DeFi, where the stakes are high, investing in top-notch security audits is not just a precaution—it's a necessity.
Secure your protocols, protect your assets, and build with confidence knowing that your security is in expert hands.
Contents



