How Self-Transfers Turned Into a Labubu Token Exploit?
Discover how flawed transfer logic led to the LABUBU token exploit on BSC, causing massive losses via flash loans and token swaps. Learn how it could've been prevented.

What Went Down on December 10th?
On December 10, 2024, the Labubu Token on the Binance Smart Chain (BSC) was exploited due to a flaw in its transfer logic. The vulnerability allowed an attacker to manipulate the token's balance system and increase his own balance without properly transferring the token.
Too Long, Didn’t Read (TLDR):
- The LABUBU token on Binance Smart Chain got exploited due to flawed transfer logic.
- An attacker used a flash loan to exploit a loophole allowing self-transfers, increased their balance for free, and laundered the stolen funds via token swaps.
- The root cause: Missing a critical check in the transfer function.
Which Contracts Took the Hit?
Attacker’s address: 0x27441c62dbe261FDF5e1feec7eD19cF6820D583b
Attacker’s contract addresses: 0x2Ff0Cc, 0x5CB78b
Vulnerable contract: 0x2fF960F1D9AF1A6368c2866f79080C1E0B253997
Attack transaction: 0xb06df37
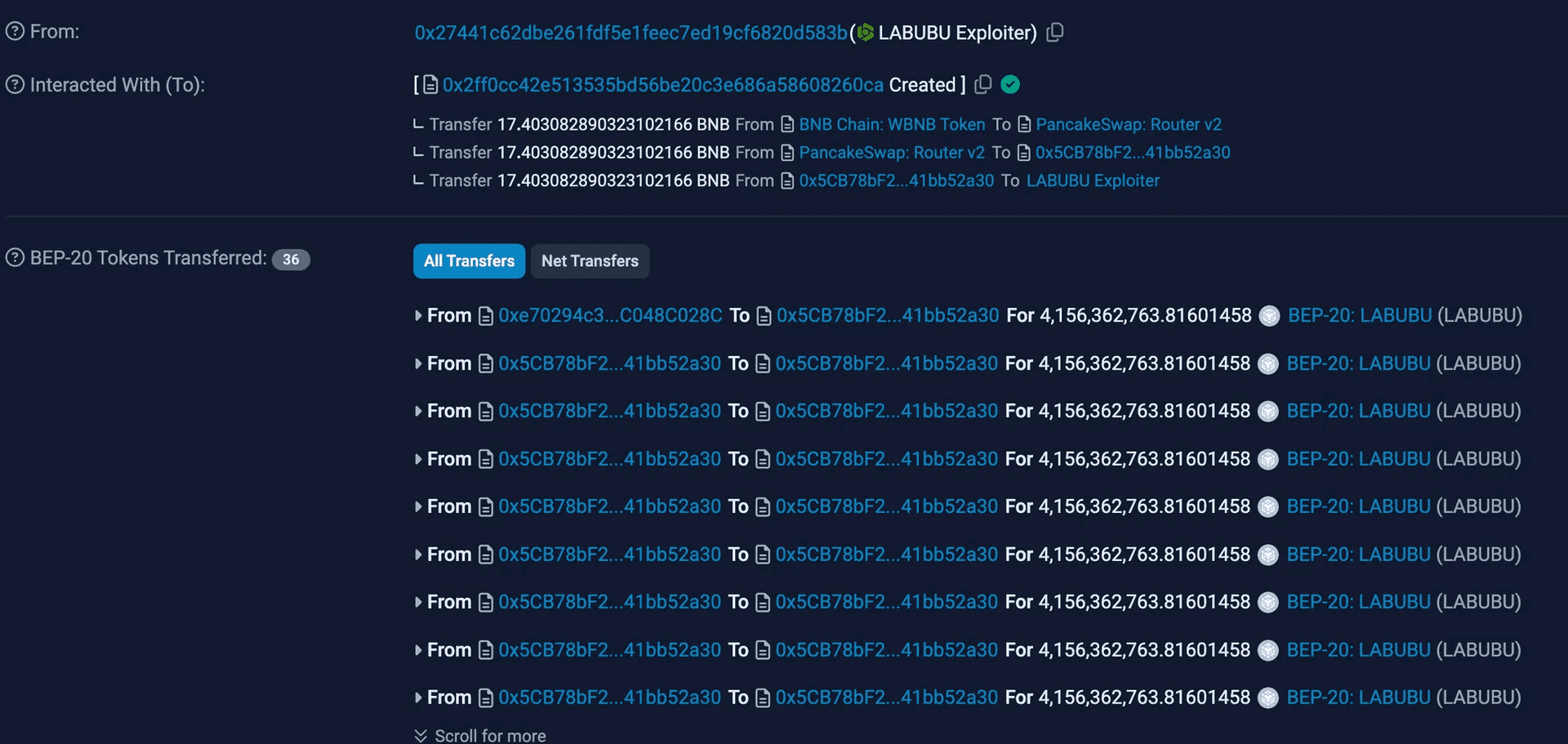
How Did the Attack Play Out?
- Initial Setup: The attacker utilized a PancakeSwap V3 pool flash loan to borrow 4,156,362,763 LABUBU tokens.
- Exploitation of Incorrect Logic: After receiving the tokens, the attacker exploited the flawed transfer logic in the LABUBU token contract.
- The transfer function allowed the same address to be used as both the sender and receiver.
Upon execution, the sender's balance decreased by the transferred amount and the recipient's balance increased by the same amount due to the incorrect logic.
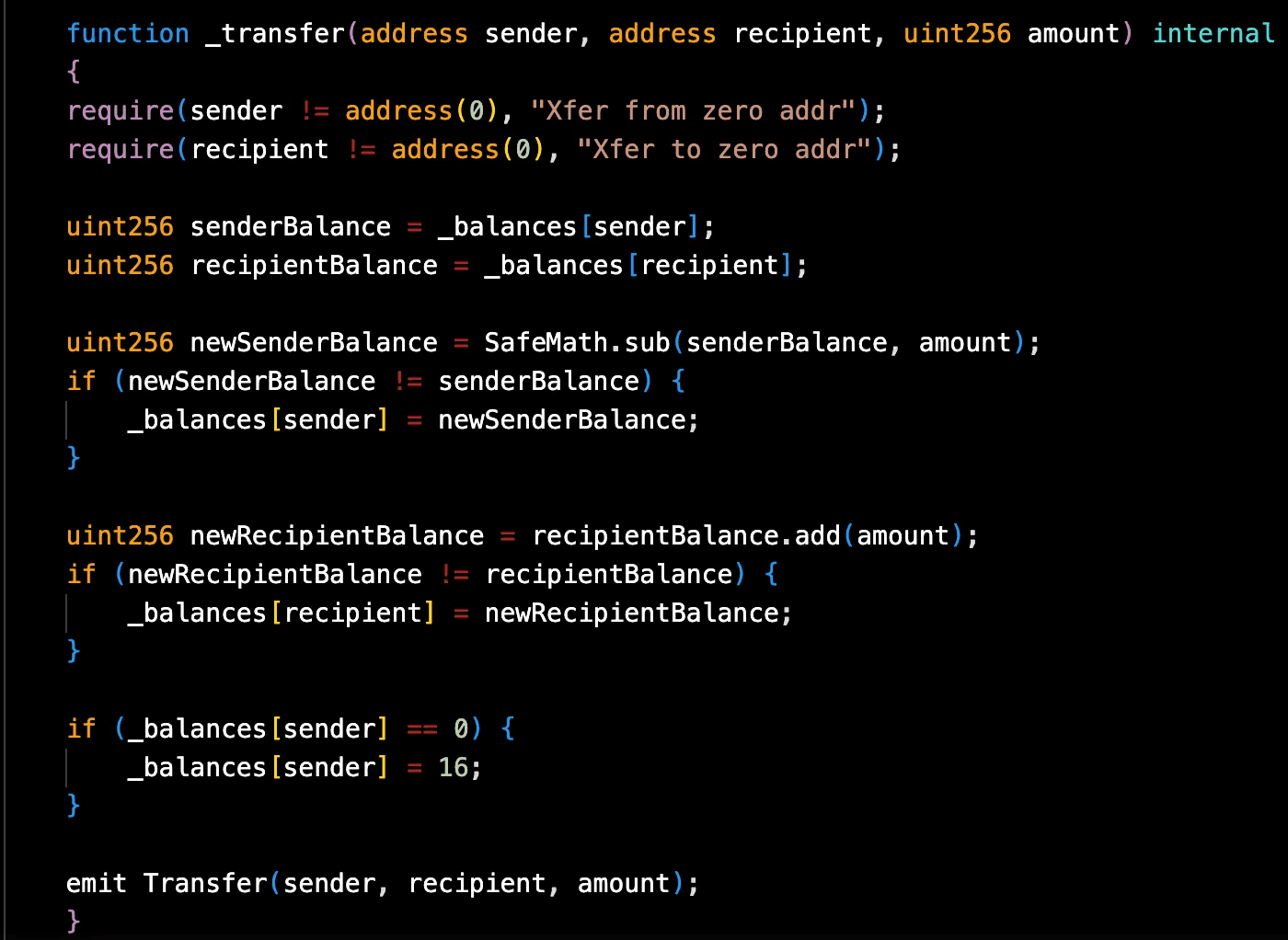
- Since the sender and receiver were the same address, the net effect was a permanent increase in the attacker's token balance.
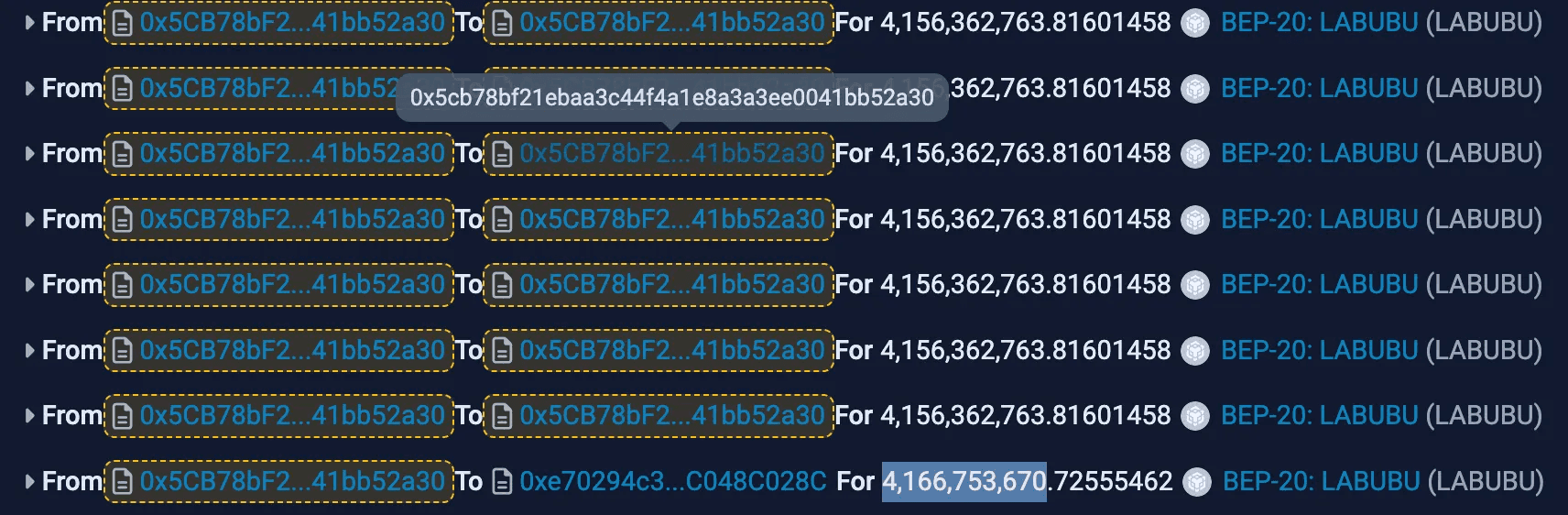
- The attacker repeatedly executed this flawed transfer logic, compounding their token balance with each iteration.
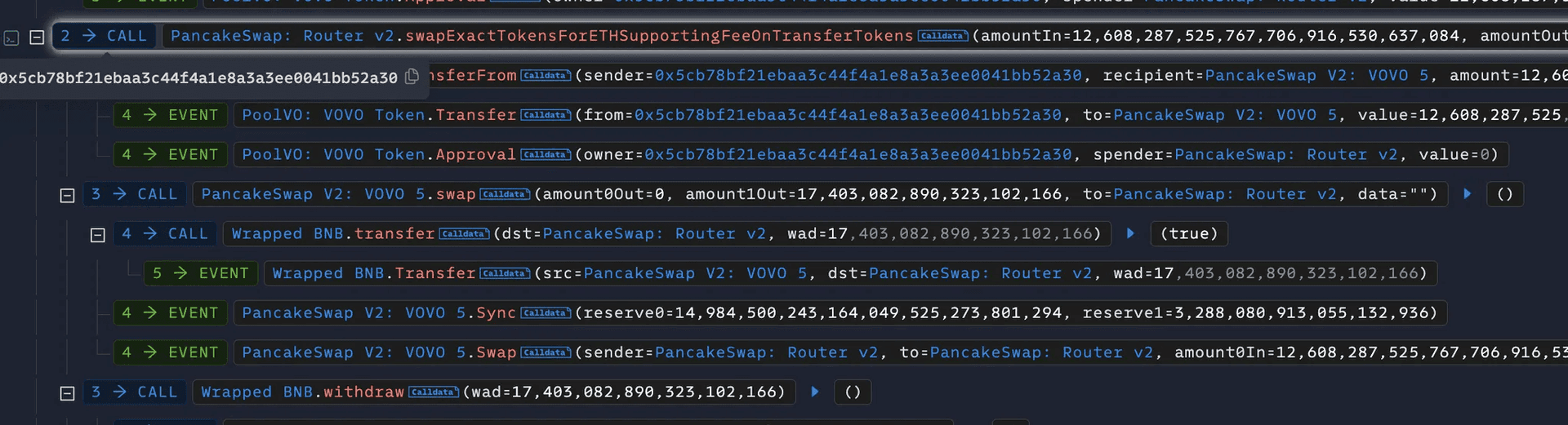
The attacker then swapped these siphoned LABUBU tokens for 12,608,287,525 VOVO tokens on PancakeSwap.
Following this, the attacker exchanged the VOVO tokens for 17 BNB, successfully laundering the stolen funds.
Why Did This Happen? What’s the Root Cause?
The root cause lay in the transfer function's failure to prevent the same address from being used as both the sender and receiver, allowing an unintended balance inflation.
Follow the Money: Where Did It All Go?
Dive into the funds flow here:

How Could This Have Been Prevented?
- Collaborate with reputable audit firms like QuillAudits to analyse smart contracts and identify vulnerabilities.
- The transfer function should include checks to ensure the sender and receiver addresses are not the same.
- Write test cases specifically designed to validate edge cases, such as transfers to the same address.
Why QuillAudits?
Choosing a reputable smart contract audit firm like QuillAudits ensures that your protocol undergoes rigorous scrutiny from experienced security professionals. QuillAudits specializes in uncovering critical vulnerabilities and providing actionable remediation strategies. Our expertise helps safeguard your project from attacks, ensuring that security issues are addressed proactively.

Contents




