Decoding Earning Farm’s $528k Exploit
Discover how Earning Farm’s $528k Exploit happened, its Vulnerability Analysis & Impact. Read our analysis of the hack.

Summary
On the 9th of August 2023, Earning Farm from Aave protocol was attacked. The attack was made possible by a reentrancy vulnerability. And around $528k was stolen by the exploiter from the exploit.
About Project
Earning Farm is a set of smart contracts that manage crypto assets. To learn more about them, check out their website.
Vulnerability Analysis & Impact
On-Chain Details
Attacker Address: 0xee4b3dd20902Fa3539706F25005fa51D3b7bDF1b
Victim Contract: 0xFe141C32E36Ba7601D128F0C39DEdBE0F6aBb983
Attack Transaction: 0x6e6e556a5685980317cb2afdb628ed4a845b3cbd1c98bdaffd0561cb2c4790fa
The Root Cause
Although the root cause of the attack was reentrancy but a flawed business logic in burning the shares was also responsible for increasing the impact of the attack.
The withdraw() function was the function that the attacker reentered.
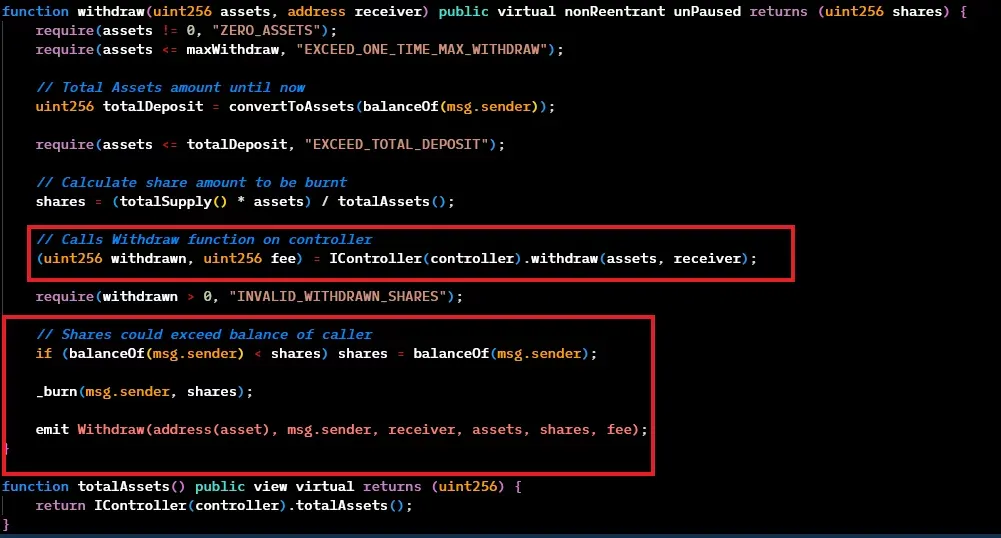
Notice how the withdrawing process is executed before burning the shares.
Upon close analysis a logical flaw was spotted.
- If the sender has somehow less share than needed to be burnt, then only their balance will be burned.
- Hence, when updating the balance of the `msg.sender` later, the result of `balanceOf` is already zero.
Attack Process
- First, the attacker took a FlashLoan of 10k ETH.
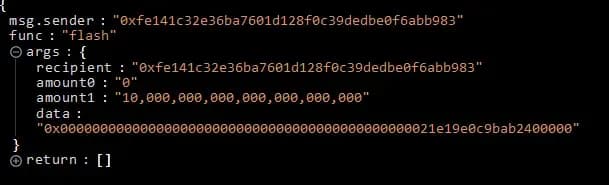
- The attacker then deposited 320 ETH into leveraged eth strategy of Earning Farm yield.
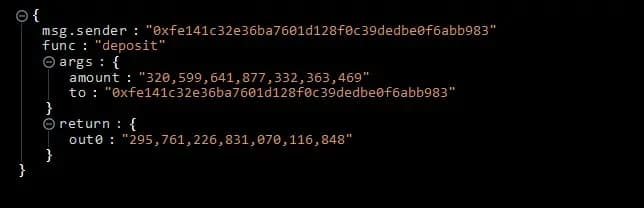
- Soon after that, the attacker withdrew the amount resulting in the attacker getting the sent eth.
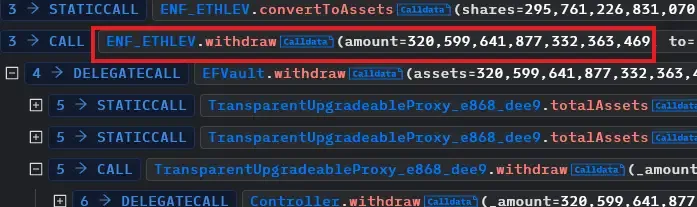
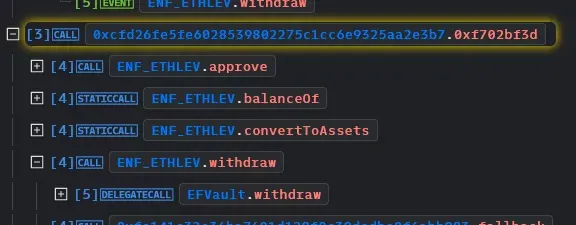
- The attacker then sent those shares to another contract that he created
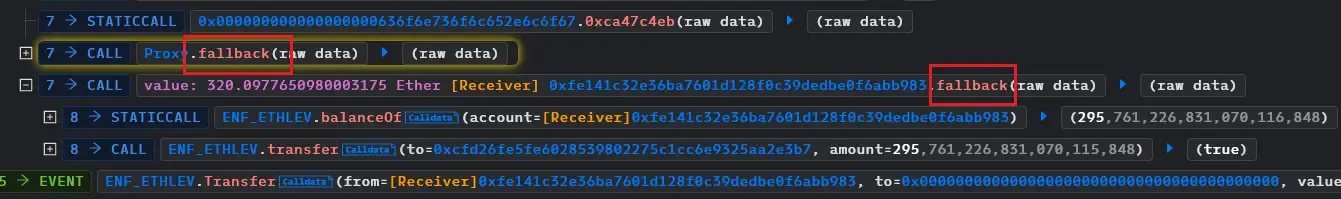
- Due to the flawed logic, nothing was burned from the attacker’s balance and he was able to get his original amount back. Then the remaining shares that were sent were also exchanged to execute the heist.
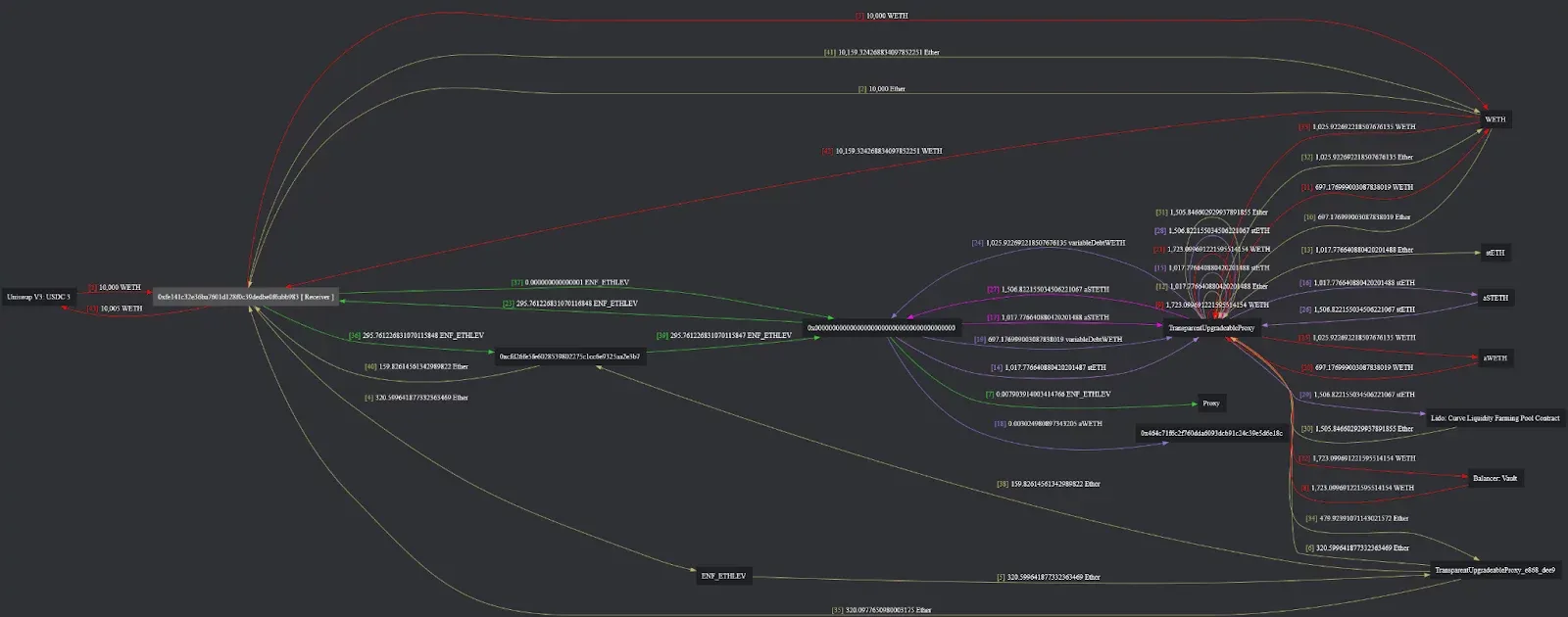
Flow of Funds
Here is the fund flow during and after the exploit. You can see more details here.
Attacker’s Wallets
Currently, all the funds residing in a bundle of 4 addresses with the majority of funds in these –
0x9d5765ae1c95c21d4cc3b1d5bba71bad3b012b68
0xe0afadad1d93704761c8550f21a53de3468ba599
Here is a snippet of one of the wallet address
After the Exploit
The Project hasn’t acknowledged the attack as of now.
Incident Timelines
Aug-09-2023 07:34:23 AM +UTC – A suspicious transaction was spotted on stETH to/from Aave Protocol.
Aug-09-2023 07:41:59 AM +UTC – Another suspicious transaction was spotted.
Aug-10-2023 02:49:11 AM +UTC – The attacker transferred the stolen funds to multiple different addresses.
How could they have prevented the Exploit?
- When dealing with business logic, it is crucial to write comprehensive Test Cases.
- A non reentrant modifier is sometimes not enough to prevent reentrancy. It is important to analyze the flow of the contract and to carefully examine the exit points of the attacker.
Why QuillAudits For Web3 Security?
- QuillAudits is well-equipped with tools and expertise to provide cybersecurity solutions saving the loss of hundreds of protocols in funds.
- Our team of highly skilled auditors have secured over 1M lines of code and $3B in amount.
- Over the course of multiple years, QuillAudits has been proven to be one of the top choices for protocols to get their codebases audited.
Partner with QuillAudits
- OG Program (Opportunities for Listing Managers, KOLs, Top Advisors and Investors with access to early stage Web3 projects)
- QuillAudits Partnership Programme (Venture funds, launchpads, development companies, marketing firms, web2 cybersecurity firms, web3 products)
- WAGSI Program(Claim audit credits to avail exclusive discounts on our auditing package, and additional credits for our automated web3 security infra- QuillShield)
Contents