How Wrong Transfer Logic Led to DCF Token Hack
Discover how flawed transfer logic led to the $428K DCF token hack. Learn key vulnerabilities, attack breakdown, and prevention strategies for securing DeFi projects.
What Happened to DCF Token?
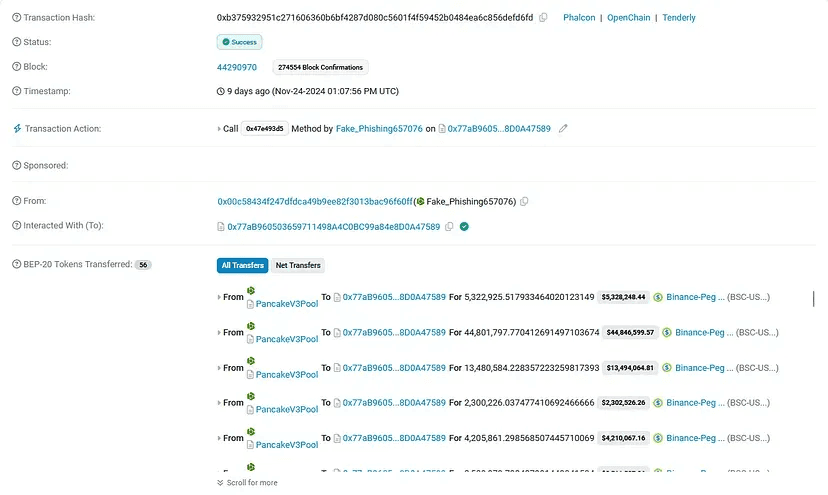
On November 24, 2024, the DCF token on Binance Smart Chain (BSC) fell victim to an exploit targeting its flawed transfer mechanism.
This breach enabled an attacker to siphon off over $428,000 USD, leaving the project reeling from liquidity loss and trust erosion.
Too Long, Didn’t Read (TLDR)
- On November 24, 2024, the DCF token on Binance Smart Chain was hacked, causing a loss of $428,000.
- The attack exploited a flaw in the token’s transfer mechanism, which triggered swaps on PancakeSwap, allowing price manipulation.
- An unnecessary burn function further drained liquidity.
- Key issue: Lack of safeguards in the transfer and liquidity mechanism.
Where Did It Go Wrong?
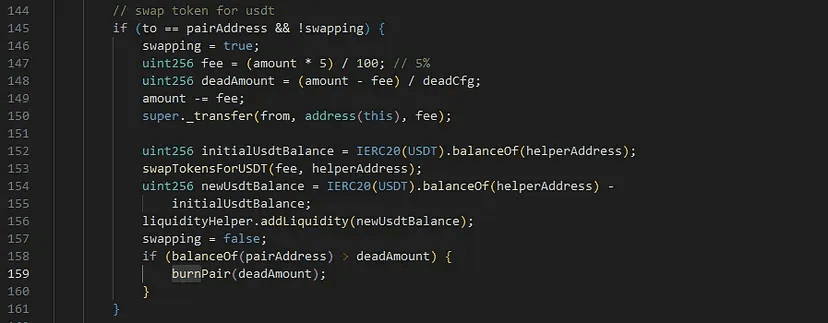
At the heart of the exploit was a vulnerability in DCF's transfer function, which automatically converted 5% of transferred tokens into USDT and added them to the USDT-DCF liquidity pool. While this mechanism was intended to maintain liquidity, it inadvertently became a gateway for price manipulation.
The issue? Every transfer to the liquidity pool triggered a swap on PancakeSwap.
This behavior allowed the attacker to execute a calculated series of trades and manipulate token prices to their advantage.
How Did the Attack Unfold?
Here’s the step-by-step breakdown:
- Funding the Exploit: The attacker borrowed a significant amount of USDT to fund the operation.
- Price Manipulation: The borrowed USDT was used to buy DCF and DCT tokens, transferring DCF to the PancakeSwap liquidity pool.
- Triggering the Mechanism: The liquidity addition triggered the automatic swap mechanism, artificially inflating the DCT token price.
- Exploiting the Loophole: The attacker capitalized on the inflated price by swapping DCT tokens back into USDT, netting a substantial profit.
- Collateral Damage: An unnecessary burn function in the smart contract further depleted the DCF token reserves in the liquidity pool, exacerbating the damage.
Attack details:
- Attacker Address: 0x00c58434f247dfdca49b9ee82f3013bac96f60ff
- Vulnerable Contract: 0xa7e92345ddf541aa5cf60fee2a0e721c50ca1adb
- Attack Transaction: 0xb375932951c271606360b6bf4287d080c5601f4f59452b0484ea6c856defd6fd
Why Did This Vulnerability Exist?
The transfer function’s automatic liquidity mechanism lacked safeguards against:
- Unchecked token burns: The burn mechanism unnecessarily depleted token supply, weakening the pool.
- Price manipulation vulnerabilities: The protocol didn’t validate liquidity swaps or the resultant price impact.
In hindsight, these flaws highlight the perils of deploying under-audited contracts with complex tokenomics.
How Could This Have Been Prevented?
Rigorous Smart Contract Audits:
A comprehensive audit could have flagged the faulty transfer mechanism, liquidity swap logic, and unnecessary burn function. Security partners like QuillAudits specialize in identifying such flaws before deployment.
- Mitigation of Price Manipulation Risks:
- Implementing price oracles with time-weighted average price (TWAP) safeguards would have mitigated sudden price swings.
- Adding a transfer validation layer to check swap thresholds would prevent excessive manipulation.
Regular Testing of Tokenomics:
Tokenomics mechanisms should be stress-tested against edge cases to ensure they cannot be abused.
Final Thoughts
The DCF token hack serves as another grim reminder that complex tokenomics without adequate safeguards are ticking time bombs.
As DeFi projects race to innovate, security must not take a backseat. Deploying unaudited or under-tested protocols is not just reckless—it’s irresponsible.
The ecosystem thrives on trust, and it’s time for teams to prioritize their users' safety.
Investing in robust security measures is always cheaper than enduring the fallout of a multimillion-dollar exploit.
Decision is up to you.
Why QuillAudits?
Choosing a reputable audit firm like QuillAudits ensures that your protocol undergoes rigorous scrutiny from experienced security professionals. QuillAudits specializes in uncovering critical vulnerabilities and providing actionable remediation strategies.
Our expertise helps safeguard your project from attacks, ensuring that security issues are addressed proactively.

Contents




