What Went Wrong in BYC Token’s $100K Hack?
BYC Token's $100K hack exposed flaws in its autoBurnLiquidity function. Read our in-depth analysis to understand the exploit and lessons learned. Stay secure with QuillAudits.

Overview
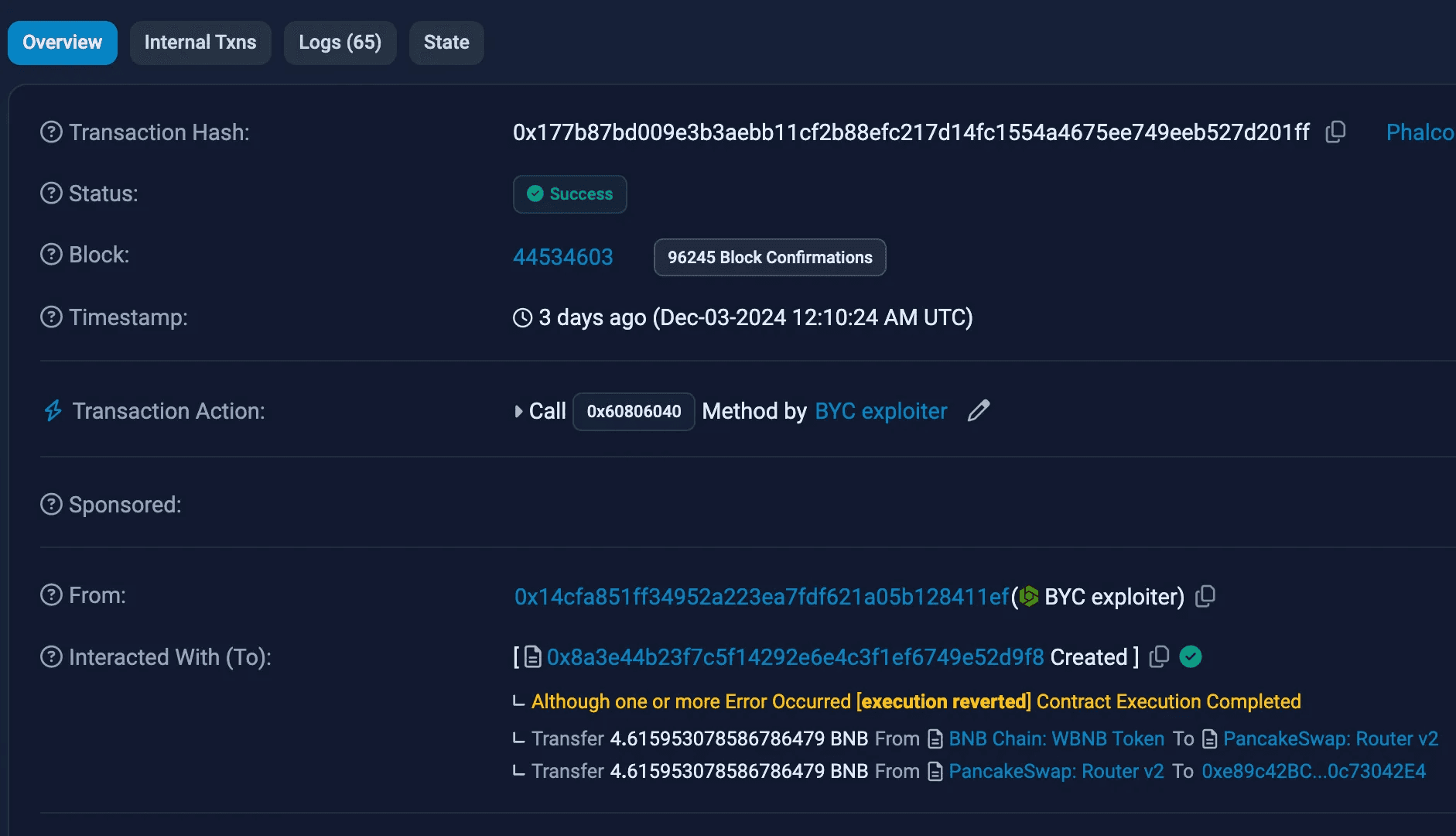
On Dec-03, 2024, BYC token got exploited due to a vulnerability in the “autoBurnLiquidity” function. The hacker manipulated the “lpBurnFrequency” parameter by exchanging a large amount of USDT for BYC and transferring all BYC to the PancakeSwap pair, which inflated the parameter's value. By calling "autoBurnLiquidity," the attacker reduced the BYC reserve to 1, enabling him to drain all USDT from the liquidity pool, resulting in a $100k loss.
Exploit Details
- Attacker Address:
0x14CfA851ff34952A223Ea7fDF621a05B128411ef - Attacker Contract Address:
0x9B227,0x0x8a3e - Vulnerable Contract Address:
0x9A69eB74060e2808344Ac35Bb5825051B89BBE76 - Attack Transaction:
0x177b87b
Attack Process
The
autoBurnLiquidityfunction in the BYC contract is designed to burn tokens by transferring them from the PancakeSwap liquidity pool to the DEAD address.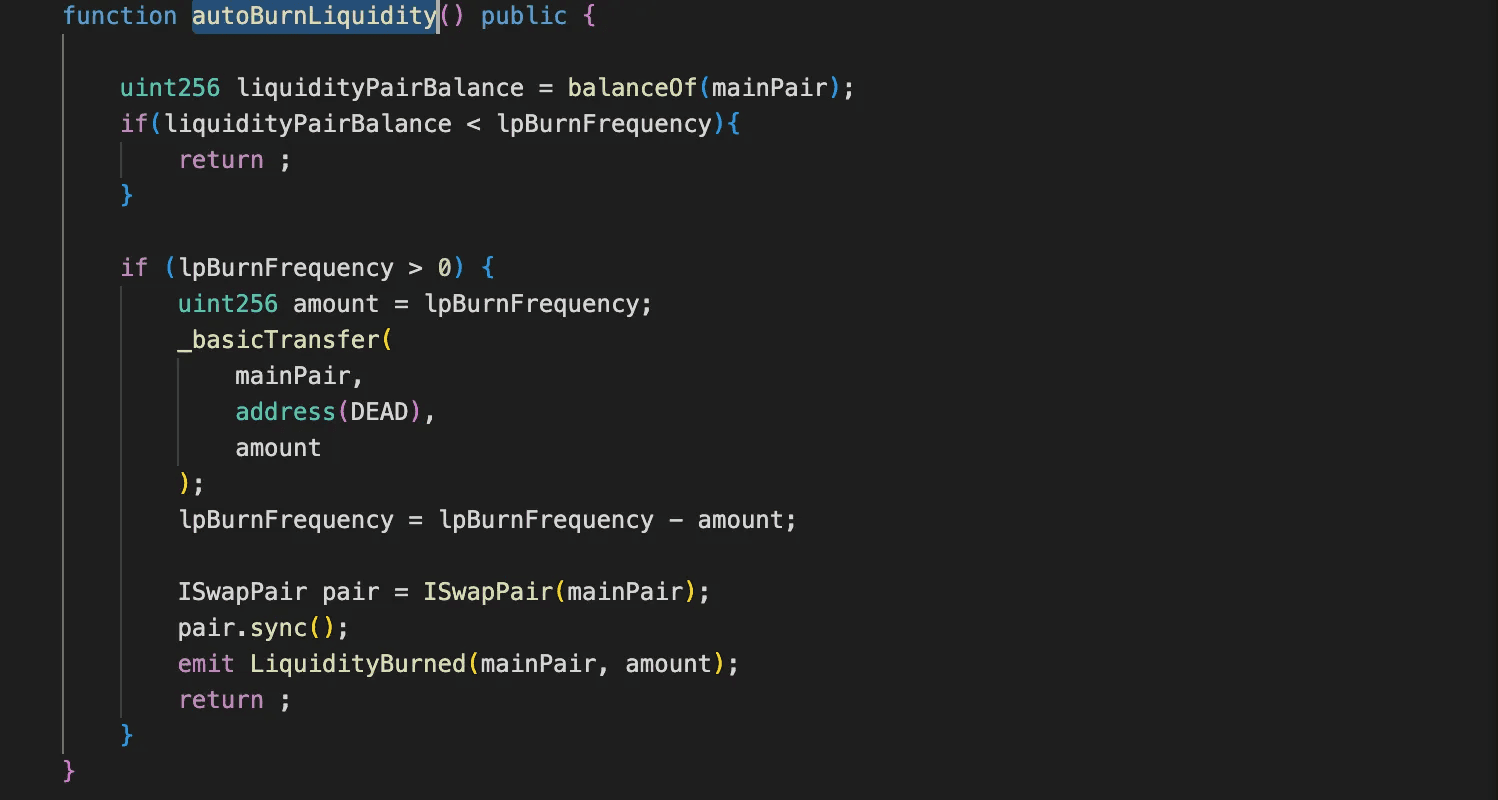
- The function is triggered when the balance of the pancake pair exceeds a threshold defined by the
lpBurnFrequencyvariable. The value of
lpBurnFrequencyincreases when tokens are transferred to the pancake pair (for example, during exchanges of BYC for USDT).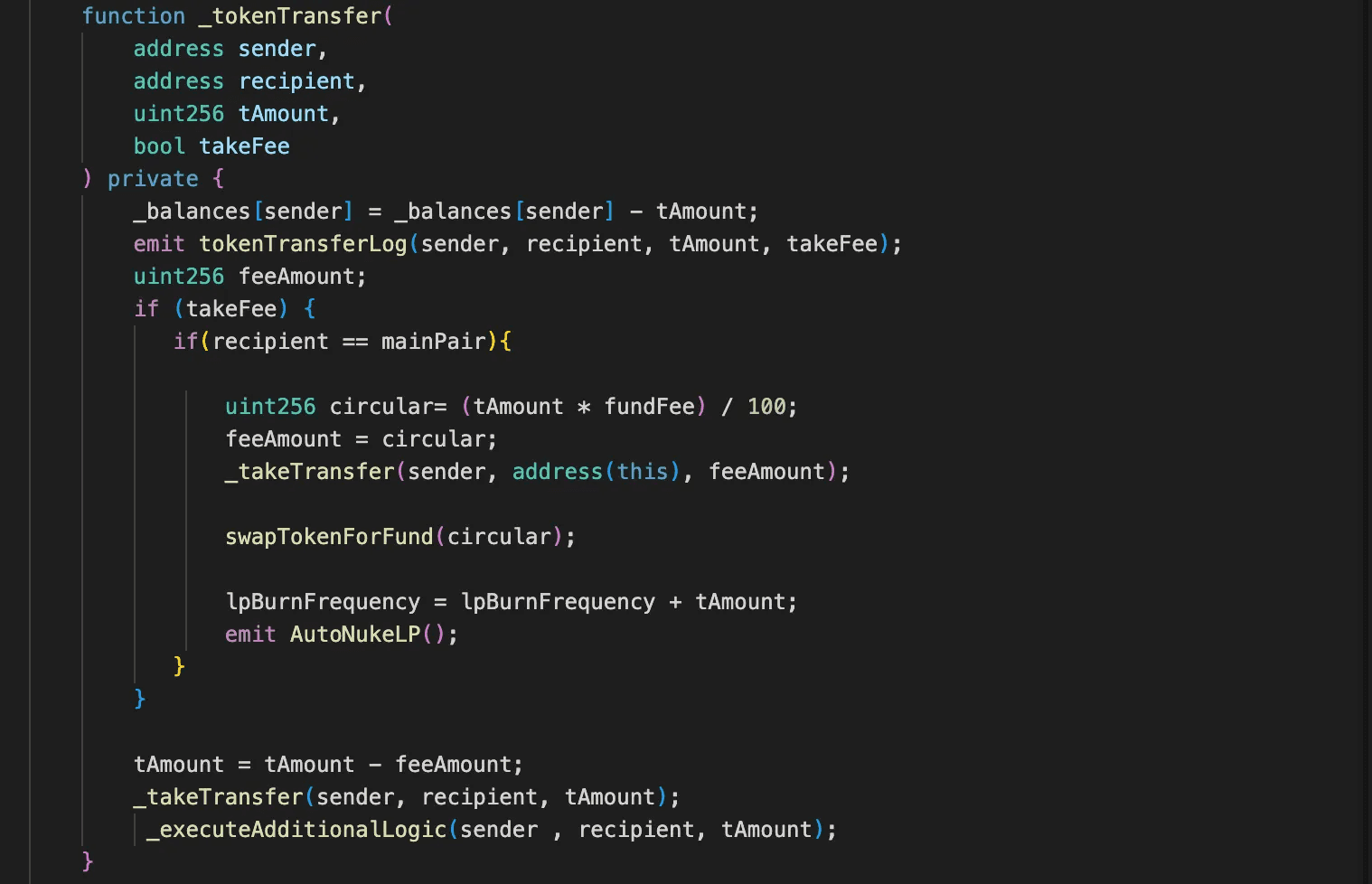
- The attacker identified that by transferring a large amount of BYC tokens to the pancake pair, he could artificially increase the
lpBurnFrequencythreshold. Once this threshold was manipulated, the attacker exploited the functionality of
autoBurnLiquidityto drain the liquidity pool.
- After the
autoBurnLiquidityfunction execution, the BYC reserve in the liquidity pool was reduced to just 1 BYC. - The extreme imbalance in the reserves of BYC and USDT caused the price of USDT relative to BYC to drop dramatically.
- With the BYC reserve effectively drained, the attacker was able to extract almost all the USDT from the liquidity pool.
- This resulted in a total loss of approximately $100,000 worth of USDT.
The Root Cause
The root cause of the exploit lies in the autoBurnLiquidity function's reliance on the lpBurnFrequency parameter, which was manipulatable through token transfers to the liquidity pool. The function failed to impose limits or validation checks on how lpBurnFrequency could be increased, allowing the attacker to inflate it artificially. Once inflated, the function burned a disproportionate amount of BYC tokens from the pool, creating an imbalance in the reserves.
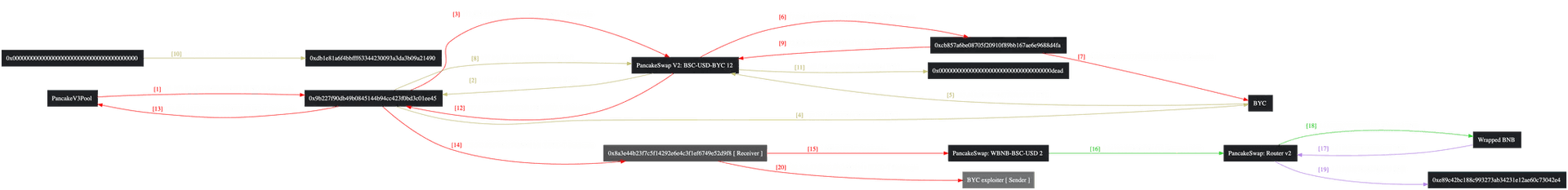
Flow of Funds
See the funds flow here:
How could they have prevented the Exploit?
- Adding logic to ensure that
autoBurnLiquidityonly executes when specific, well-defined conditions are met, such as requiring a minimum balance or specific time intervals between burns. - Introduce strict rate limits or maximum bounds for how much
lpBurnFrequencycan increase to prevent malicious inflation. - Collaborate with reputable auditors like QuillAudits to analyse smart contracts and identify vulnerabilities.
Why QuillAudits?
Choosing a reputable audit firm like QuillAudits ensures that your protocol undergoes rigorous scrutiny from experienced security professionals. QuillAudits specializes in uncovering critical vulnerabilities and providing actionable remediation strategies. Our expertise helps safeguard your project from attacks, ensuring that security issues are addressed proactively.

Contents



