Déjà Vu! How a Previously Patched Vulnerability Led to Astroport’s $6.4M Exploit
Learn how a previously patched vulnerability led to Astroport’s $6.4M exploit, analyzed by QuillAudits, and discover key issues and prevention strategies.

Summary
On July 30th, 2024, Terra (Phoenix chain) experienced a catastrophic breach due to a reentrancy vulnerability linked to IBC hooks. The attack resulted in the loss of approximately $6.4 million, which included 60M $ASTRO, 3.5M $USDC, 500K $USDT, and 2.7 $BTC.
The vulnerability was known and patched in April 2024 but was accidentally reintroduced in a June upgrade. This incident highlights serious gaps in security practices and the impact of regulatory actions.
Terra chain had been halted for emergency upgrades, and steps are being taken to address the issue and prevent future exploits.
TL;DR
- Incident: Astroport, a DEX on Terra (Phoenix chain) suffered a major exploit on July 30th, 2024.
- Vulnerability: Reentrancy issue linked to IBC hooks, reintroduced in a June upgrade after being patched in April this year.
- Losses: 60M $ASTRO, 3.5M $USDC, 500K $USDT, 2.7 $BTC. Approximately $6.4 million in total worth.
- Attack Process: Contract instantiation followed by an IBC transfer timeout, allowing fund siphoning.
- Response: Terra chain was halted for emergency upgrades; steps were taken to address the vulnerability.
- Fund Recovery: The remaining 20 million $ASTRO tokens that had not yet been moved by the attacker were frozen on the Terra chain. The $ASTRO tokens held in the exploiter's wallet on Neutron were forcibly transferred back to a secure wallet controlled by the recovery team.
- Regulatory Impact: SEC actions led to reduced capacity for Terra's development team, impacting their ability to maintain security and respond to vulnerabilities effectively. This included layoffs and resource constraints that delayed critical updates and patches.
- Attacker’s address on Terra: terra1wrve5z5vsmrgy6ldcveq93aldr6wk3qmxavs4j
- Attacker’s address on Neutron: Neutron16wynag7xgfy35sp8c5ls25c0je7dydmvq5pnd8
- Bridge Transaction: 7E28A2BDD3A6DBED27269C23D0BDA2FBE4B2BE7F613E87CC23A237DA473F14E2
- Address on Ethereum: 0xBDe173c4C2249d3a98cD6ed844a4421728114F5A
- Astroport Router Contract: https://chainsco.pe/terra2/address/terra18plp90j0zd596zt3zdsf0w9vvk5ukwlwzwkksxv9mdu8rscat9sqndk5qz
- Attack Transaction: https://www.mintscan.io/terra/tx/4F260BFD0D9357859A186D1EDD9CF6CEDF4EA521D1595CB7823DE22D6084DDA0?height=11426811
- Instantiate Contract & IBC Channel Timeout Method Execution: https://chainsco.pe/terra2/address/terra1wrve5z5vsmrgy6ldcveq93aldr6wk3qmxavs4j?page=4
- IBC Implementation: https://github.com/cosmos/ibc-go/security/advisories/GHSA-j496-crgh-34mx

Check Out Our Work
We've audited top DApps and DeFi protocols, ensuring they remain secure and Free from Hacks. Check out their audit reports to see our impact.

A Step-by-Step Breakdown of How The Exploit Happened
Step 1: Contract Instantiation & IBC Transfer
The exploit began with the instantiation of a malicious CosmWasm contract on the Terra blockchain. , followed by an IBC transfer that timed out. The contract was instantiated from Code ID 3114 in transactions such as 11426889 and 11426885. This sequence of events allowed the attacker to initiate the exploit.
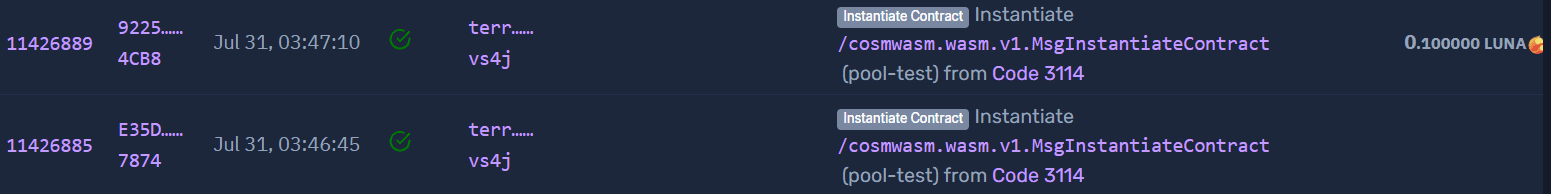
Step 2: Exploiting the Reentrancy Vulnerability
The vulnerability exploited was related to IBC hooks and involved reentrancy. By executing a malicious CosmWasm contract via IBC interactions, the attacker could recursively execute the same MsgTimeout inside the IBC hook for the OnTimeout callback before the packet commitment was deleted. This allowed for the siphoning of funds.
Specifically, transactions like 11426330 show the transfer of 300,000 axlUSDC from the attacker's Terra address to an Axelar address. The IBC protocol includes mechanisms for acknowledging and updating clients across chains, which the attacker used to their advantage.
The attacker executed IBC transfer transactions followed by inducing IBC channel timeouts (as seen in transactions 11427203, 11427189, 11427186, 11427185, etc.). This timeout allowed the malicious contract to reenter and execute unintended additional transactions.
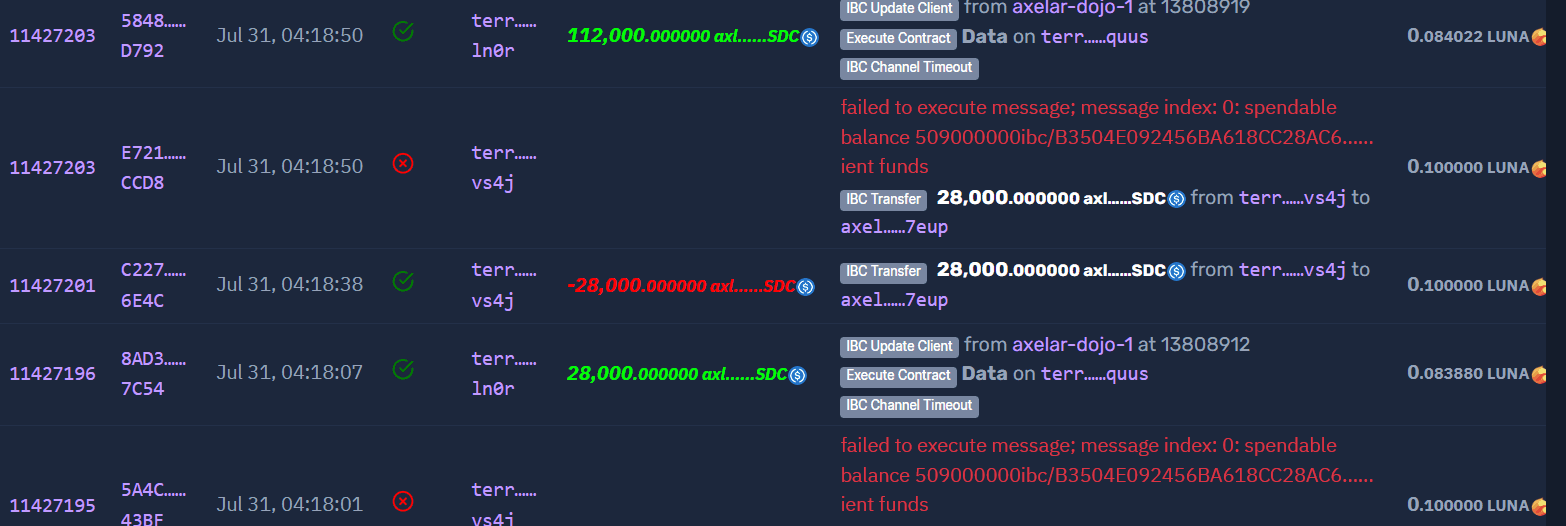
Step 3: Contract Execution & Fund Siphoning
The attacker executed multiple contract interactions that manipulated the IBC channel's state to reenter the contract execution process. This reentrancy allowed the attacker to siphon funds by exploiting the timeout mechanism.
For example, in transaction 11427207, the attacker successfully transferred 112,000 axlUSDC from their Terra address to an Axelar address.
Step 4: Swapping & Diversion of Funds
The attacker utilized the Astroport Router contract to perform swaps, converting stolen USDC to other tokens like LUNA and WBTC. Transaction 11426257 illustrates the swap of 100,000 axlUSDC for 0.001342 WBTC.
The attacker continued to execute large IBC transfers to move stolen funds off the Terra chain. Notable transactions include 11427207 for 112,000 axlUSDC and multiple smaller transactions like 11427194, 11427186, and 11427155, each transferring thousands of axlUSDC.
Step 5: Lost Funds
The attacker managed to siphon approximately 60M $ASTRO, 3.5M $USDC, 500K $USDT, and 2.7 $BTC into an account. The stolen funds were then swiftly transferred out via IBC.
The Root Cause
The exploit on the Terra chain was fundamentally due to the reintroduction of a previously patched reentrancy vulnerability associated with Inter-Blockchain Communication (IBC) hooks.
In April 2024, critical patches were applied to address this specific vulnerability in the ibc-go library, which is essential for handling cross-chain transactions securely. However, during a system upgrade in June 2024, Terra inadvertently reintroduced an outdated internal fork of ibc-go version 7.3.x. This version was missing these critical patches and did not incorporate the fixes necessary to prevent such vulnerabilities.
The outdated fork, which was not aligned with the more recent and secure versions (>7.4.1), contained the old, flawed codebase. This oversight meant that while Terra's system was updated in some areas, it was not fully protected against the known reentrancy attack vector. This reintroduced vulnerability allowed attackers to exploit the IBC hooks, leading to the significant exploit on July 30th, 2024.
What Happened Afterwards: Steps Taken
Chain Halt
Following the attack, Terra chain was halted for emergency upgrades to prevent further exploitation and to address the vulnerability.
Later on the issue was fixed and the chain was resumed.
Addressing the Vulnerability
Terra's team, along with Astroport contributors and Cosmos builders, worked on identifying and mitigating the issue. The primary focus was on upgrading to the latest patched version of ibc-go and ensuring no further vulnerabilities were present.
Regulatory Oversight
The oversight that led to the reintroduction of the vulnerability raises serious questions about security practices, especially in light of regulatory actions against Terraform Labs (TFL) by the SEC. The SEC's actions, while aimed at protecting investors, may have inadvertently contributed to the oversight by reducing the capacity of the Terra team.
Actions Taken by Astroport
Astroport took significant steps to mitigate the damage and recover the stolen assets: The attackers' $ASTRO on Neutron were seized and are being held in the Astroport Treasury. The attackers' Terra address was blacklisted from making any transactions. The IBC Hook vulnerability was patched to prevent further exploitation.
Fund Tracking & Recovery
The attacker stole a total of approximately 58 million ASTRO tokens, with around 33 million ASTRO bridged to Neutron.
Approximately 13 million ASTRO were swapped for 124,000 axlUSDC and sent to an Ethereum address. Approximately 20 million ASTRO tokens remaining on Terra were blacklisted and cannot be moved.
Community and Developer Reactions
The incident highlighted the importance of heeding security warnings. Jacob Gadikian, a former prominent figure in the Cosmos ecosystem, had flagged the vulnerabilities but was largely ignored. His experience underscores the need for better security communication and response mechanisms within the ecosystem.
Preventing Future Exploits: Lessons Learned
Robust Patch Management
Ensuring that all patches are properly applied and verified is crucial. Regular audits and automated checks can help prevent the reintroduction of known vulnerabilities. Leveraging both AI-powered and manual smart contract audits from QuillAudits can significantly enhance security measures, providing thorough and continuous assessments to detect and address potential vulnerabilities promptly.
Secure Your Smart Contracts with QuillAudits
Ready to secure your smart contracts? Take the first step towards a safer blockchain journey. Request an Audit with QuillAudits today & ensure your contracts are robust and secure!
Improved Security Communication
The ecosystem needs better mechanisms for reporting and responding to security warnings. Ensuring that warnings from community members and developers are taken seriously can help prevent future exploits.
Enhanced Security Practices
Implementing advanced security practices, such as the Circuit Breaker module in the Cosmos SDK, can help mitigate the impact of future vulnerabilities. Regular security drills and updates are necessary to stay ahead of potential threats.
Contents



