Zero-Knowledge Machine Learning: A Beginner's Guide
Discover what a real-world ZKML application is, how zero-knowledge machine learning works, and why it's shaping the future of privacy in AI.

What is a real world ZKML application? It’s a practical use of Zero-Knowledge Machine Learning where sensitive data can be analyzed using AI without exposing the data itself. As data privacy becomes increasingly crucial, ZKML combines cryptography with machine learning to enable secure, private computations. From healthcare diagnostics to financial fraud detection, real-world ZKML applications are already showing how we can harness AI while keeping user data confidential.
In this guide, we break down the basics of ZKML, how it works, and where it's being used in the real world.
What Are Zero-Knowledge Proofs (ZKPs)?
Imagine you have a secret and need to prove you know it without spilling the beans. That’s the magic of Zero-Knowledge Proofs (ZKPs). First introduced in the 1980s, ZKPs let one party (the prover) show another party (the verifier) that they know any information beyond the validity of the statement itself.
Types of Zero-Knowledge Proofs
1. Interactive Zero-Knowledge Proofs
Think of it as a back-and-forth game where the verifier challenges the prover with questions until they’re convinced without ever seeing the actual secret. These require multiple rounds of interaction between the prover and the verifier. In each round, the verifier sends a challenge to the prover, who must respond correctly. This interaction continues until the verifier is convinced of the prover's knowledge without learning the knowledge itself.
2. Non-Interactive Zero-Knowledge Proofs (NIZKs)
No need for the back-and-forth here. The prover creates a proof once, and anyone can verify it without further interaction. These do not require interaction between the prover and the verifier, making them more practical for many real-world applications.

Basics of Machine Learning
Before we dive into ZKML, let’s quickly cover what machine learning (ML) is all about.
Machine Learning (ML) is a subset of artificial intelligence that focuses on developing algorithms that enable computers to learn from and make predictions based on data. The primary goal of ML is to build models that can generalize well from training data to unseen data.
This involves identifying patterns, making decisions, and improving from experience.
Here are the key components:
- Datasets: Collections of data used to train and test ML models. A dataset typically consists of input data and corresponding output labels. For instance, in a dataset for image classification, each image would be paired with a label indicating the object in the image.
- Models: Mathematical representations of data used to make predictions or decisions. Models can range from simple linear regressions to complex neural networks.
- Training: The process of optimizing a model's parameters using a dataset. During training, the model learns to map input data to the correct output labels by minimizing a loss function.
4.Inference: The process of making predictions using a trained model. Once a model is trained, it can be used to make predictions on new, unseen data.
ZKPs Meet Machine Learning: A Match Made in Privacy Heaven
ZKML is where the magic happens. It combines ZKPs with ML, ensuring privacy while enabling powerful computations. The idea is to train and use ML models without ever exposing the sensitive data involved.
ZKML is Where AI & Privacy Shake Hands
Zero-Knowledge Machine Learning brings together these two fields to enable privacy-preserving machine learning. The core idea is to perform machine learning tasks such as training and inference while ensuring that sensitive information about the data and the model remains confidential. This is achieved through a combination of cryptographic techniques and advanced machine learning methods.
In ZKML, the training and inference processes are designed to generate zero-knowledge proofs that validate the computations without revealing the underlying data. This ensures that sensitive data is not exposed during the machine learning process, addressing privacy concerns that are particularly relevant in fields like healthcare, finance, and Internet of Things (IoT).
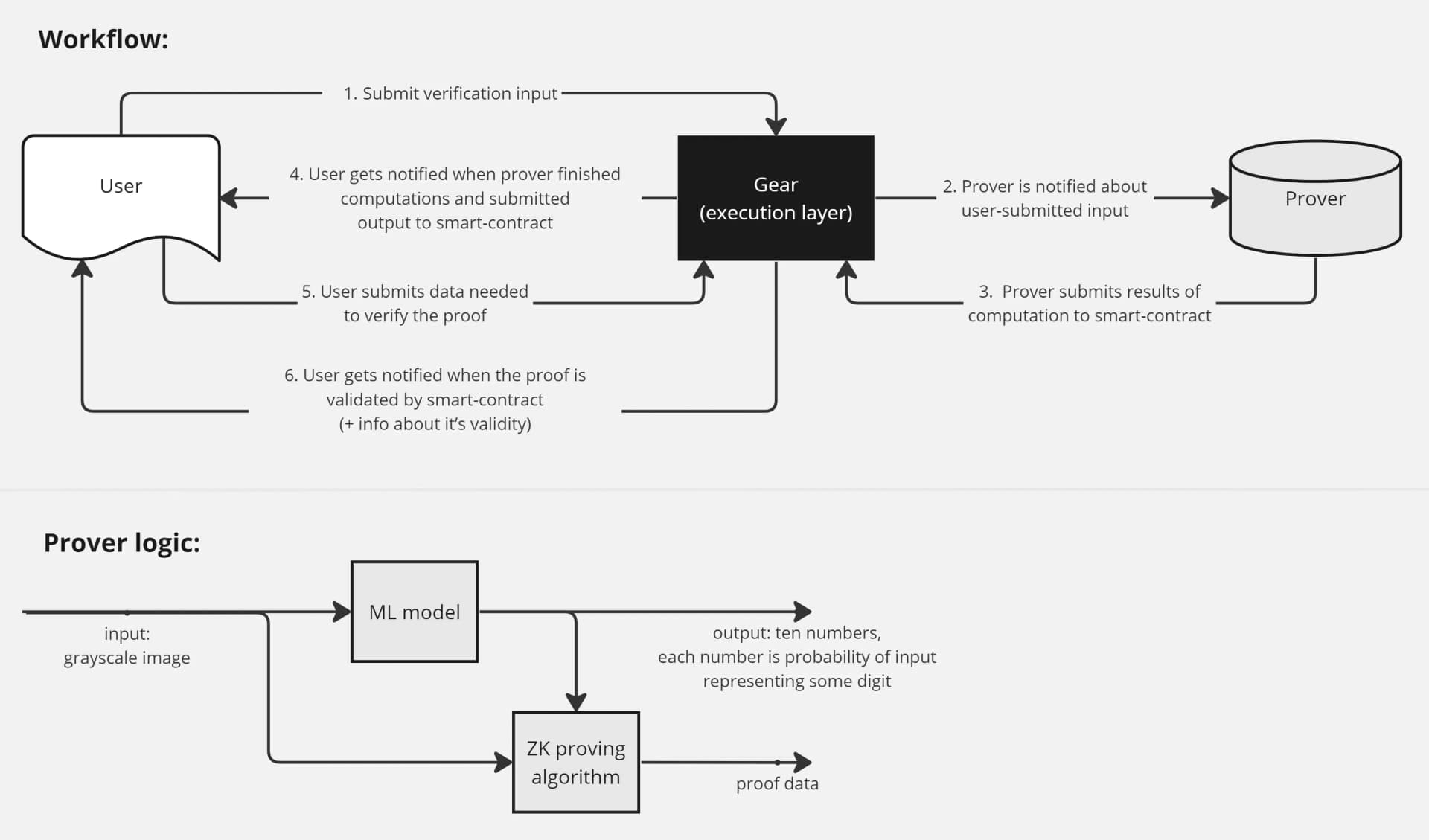
Source- https://wiki.gear-tech.io/docs/examples/Infra/zkml/
How Does ZKML Work?
Data Encryption: Before any computation begins, data is encrypted using techniques like homomorphic encryption. This ensures that the data remains secure during processing. Homomorphic encryption allows computations to be performed directly on encrypted data, generating results that can be decrypted to match the outcome of operations performed on the plaintext.
Model Training: The machine learning model is trained on encrypted data. Techniques such as federated learning can be employed, where the model is trained across multiple decentralized devices or servers holding local data samples. Each participant only has access to their data, and secure aggregation protocols ensure the privacy of local updates.
Proof Generation: During the inference phase, the trained model generates a zero-knowledge proof that it can make a prediction on the input data without actually seeing the data. This proof assures the verifier that the prediction was made correctly based on the original training data.
- Proof Verification: The verifier checks the zero-knowledge proof to confirm the validity of the prediction without accessing the input data. This verification process ensures that the model's predictions are accurate and based on the original data, maintaining privacy and security.
Techniques for ZKML
Homomorphic Encryption: Allows for computations on ciphertexts, generating encrypted results that, when decrypted, match the operations performed on plaintext. This is crucial for ensuring data remains private throughout the computation process.
Secure Multi-Party Computation (SMPC): Enables multiple parties to jointly compute a function over their inputs while keeping those inputs private. Each party's data is split into shares, and computations are performed on these shares without revealing the original data.
Differential Privacy: Involves adding noise to the data or to the results of queries on the data, ensuring that the presence or absence of any single data point does not significantly affect the outcome. This protects individual data points while allowing for useful aggregate analysis.
Federated Learning: A decentralized approach to training machine learning models across multiple devices or servers holding local data samples. The model is trained locally on each device, and only model updates (not the data) are aggregated centrally. Secure aggregation protocols ensure the privacy of these updates.
Apply for the WAGSI Grants Now!
Apply for the WAGSI Grants Now!
Take advantage of the WAGSI Grants to finance your project and implement your innovative ideas.
Real-life applications of ZKML
1. Healthcare
In healthcare, patient data is highly sensitive and protected by strict regulations. ZKML can enable the development of predictive models for diagnosing diseases or personalizing treatment plans without exposing individual patient records.
2. Finance
Financial institutions handle vast amounts of sensitive data. ZKML can be used to create fraud detection systems, credit scoring models, and personalized financial advice tools that operate without accessing users' private financial information.
3. Internet of Things (IoT)
IoT devices generate enormous amounts of data, often including personal information. ZKML can help process this data to make smart home devices, industrial systems, and autonomous vehicles more secure and privacy-conscious.
Challenges of ZKML
1. Computational Complexity
One of the main challenges of ZKML is the computational overhead associated with generating and verifying zero-knowledge proofs. Research is ongoing to develop more efficient algorithms and hardware solutions to address this issue. Techniques such as zk-SNARKs and zk-STARKs are being explored to improve performance.
zk-SNARKs: These are a type of non-interactive proof that is short and easy to verify. zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) are efficient and are used in blockchain applications like Zcash to enable private transactions.
- zk-STARKs: These offer scalability and transparency without a trusted setup, making them suitable for large-scale applications. zk-STARKs (Zero-Knowledge Scalable Transparent Arguments of Knowledge) are seen as the next generation of zero-knowledge proofs, potentially offering more efficient and secure solutions.
2. Model Accuracy
Ensuring that ZKML models maintain high accuracy while preserving privacy is another significant challenge. Striking the right balance between privacy and performance is crucial for the practical adoption of ZKML. Researchers are exploring methods to fine-tune models without compromising privacy, such as privacy-preserving training techniques and advanced regularization methods.
- Privacy-Preserving Training: Techniques like federated learning and differential privacy are used to train models without exposing individual data points. These methods help maintain model accuracy while ensuring data privacy.
- Regularization Methods: Advanced regularization techniques are employed to prevent models from overfitting to specific data points, thereby enhancing generalization and privacy.
Wrap-Up
Zero-Knowledge Machine Learning represents a significant advancement in the quest for privacy-preserving technologies. By combining the strengths of zero-knowledge proofs and machine learning, ZKML offers a promising solution to the challenges of data privacy and security. As research and development in this field continue, we can expect to see more innovative applications and improvements in efficiency and performance.
The journey of ZKML is just beginning, and its potential to transform industries by providing secure and private machine learning solutions is immense. Staying informed and engaged with this emerging technology will be crucial for anyone interested in the future of data privacy and artificial intelligence.
Contents


